2 min to read
What is Microsoft Defender Threat Intelligence
Security Analyst Workbench

Before starting let’s understand a few steps of threat investigation and attackers’ mindset. Whenever attacker breaches a system or try to all logs are generated as Events and Incidents which can be fetched into SIEM tools like MS Sentinel , Qradar. These behaviours can be summarised into TTP viz
- Tactics : The high level description of the behaviour and strategy of a threat actor.It means how they behave across the different stages of the cyberattack kill chain. Usually these stages includes :
- Reconnaissance
- Delivery and exploitation
- Acting on the objective
- Technique : This is all about what the threat actors do in order to cause all sorts of problems. eg : Network infiltrate, Inside movement without trace, command and control centers establishments
- Procedure: are the detailed description of how tactics are executed using the choice of techniques and set of actionable.
So for every SOC analyst have to visit multiples repository to check , Domain Name, IP reputations, CVE details . So to reduce the pain of SOC people Microsoft has solution called Microsoft Defender Theat Intelligence aka MDTI
What is MDTI? Platform that streamlines triage, incident response, threat hunting, vulnerability management and cyber threat intelligence analyst workflows.
USE CASES
- Security Operations :use data collection from various cyber defense tools to analyze events occuring within an environment to migrate threats.
- Incident Response: Investigate, Analysis and Responding to cyber Incidents within a network
- Threat Hunting: Search for malware and attacker within a n/w
- Cyber Threat Intelligence Analysis: Identifying and Tracking cyber threats to an organisation and working with stakeholders to reduce task.
- Cybersecurity Research: Developing a new concept and approach .
Demo
Licences : Defender TI premium Licence Free Licence can access free offering of MDTI
- Landing Page Look :-
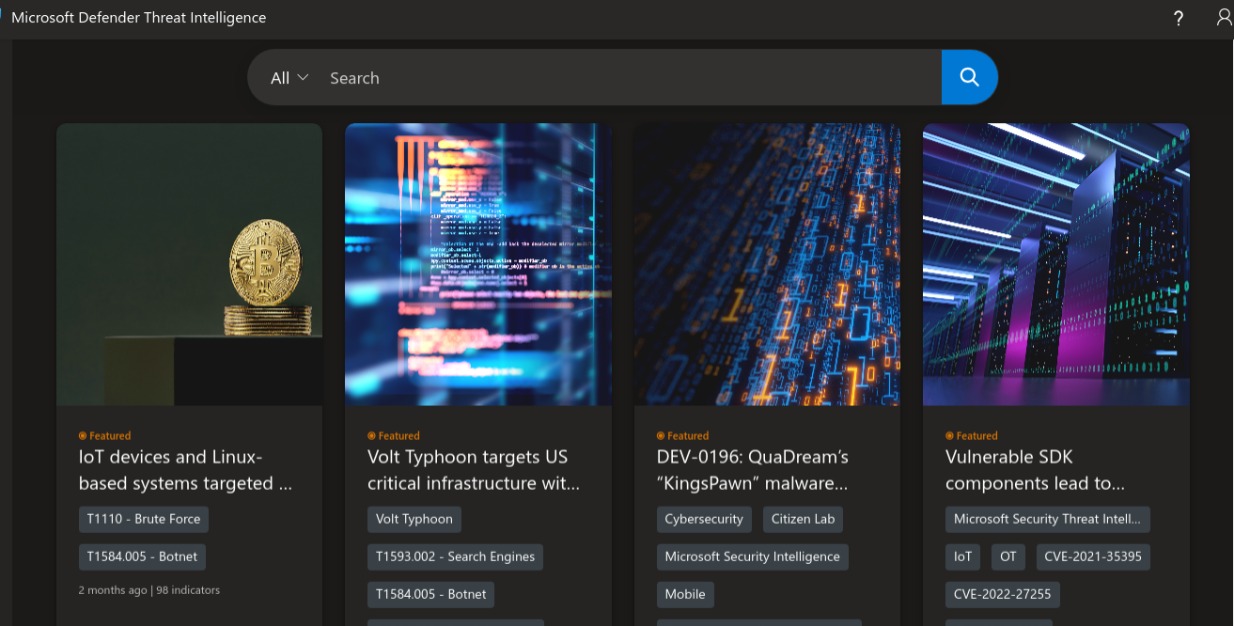
It contains featuured articles with CVE , Threat Indicators and Intel Group name
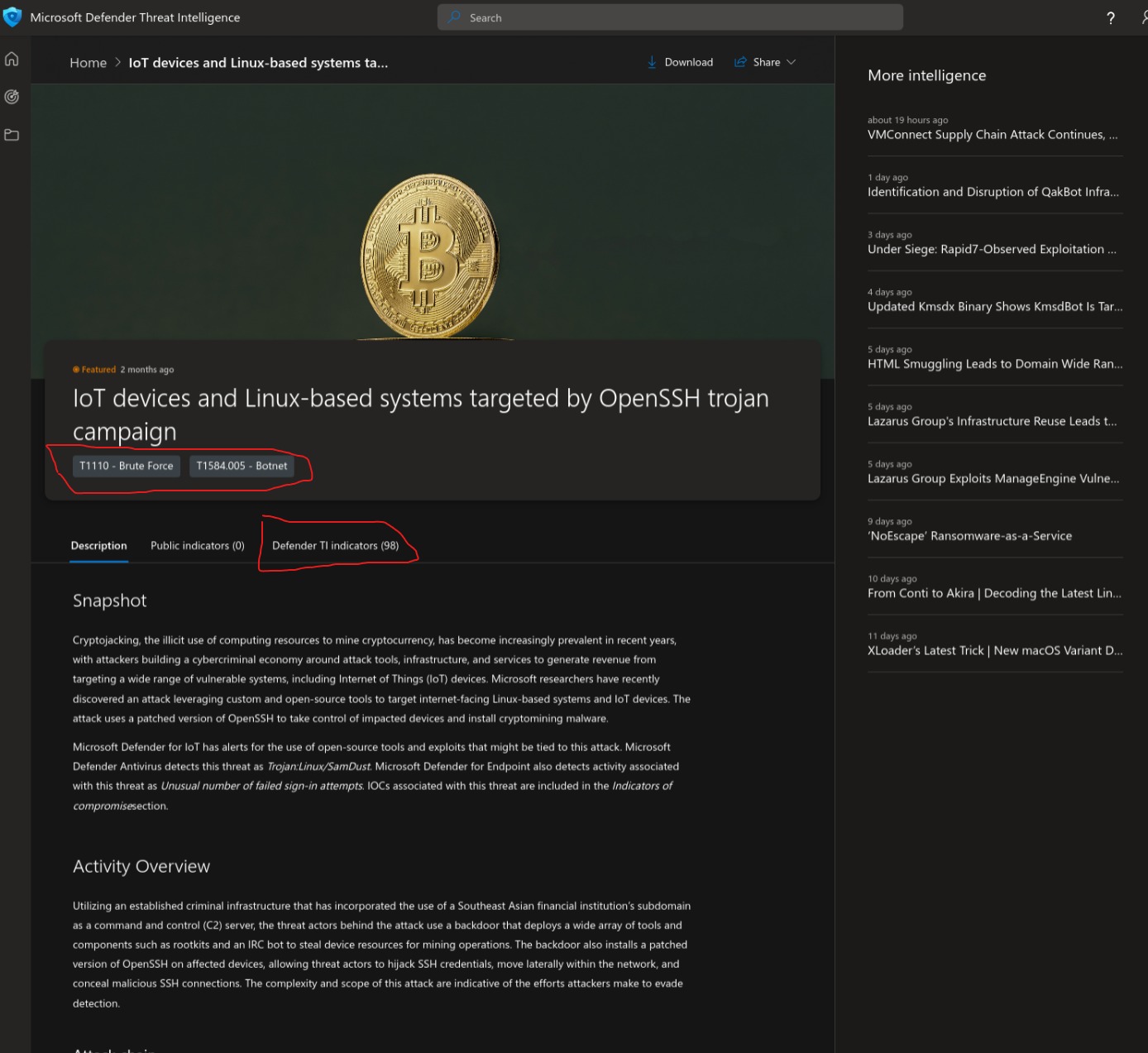
- Articles
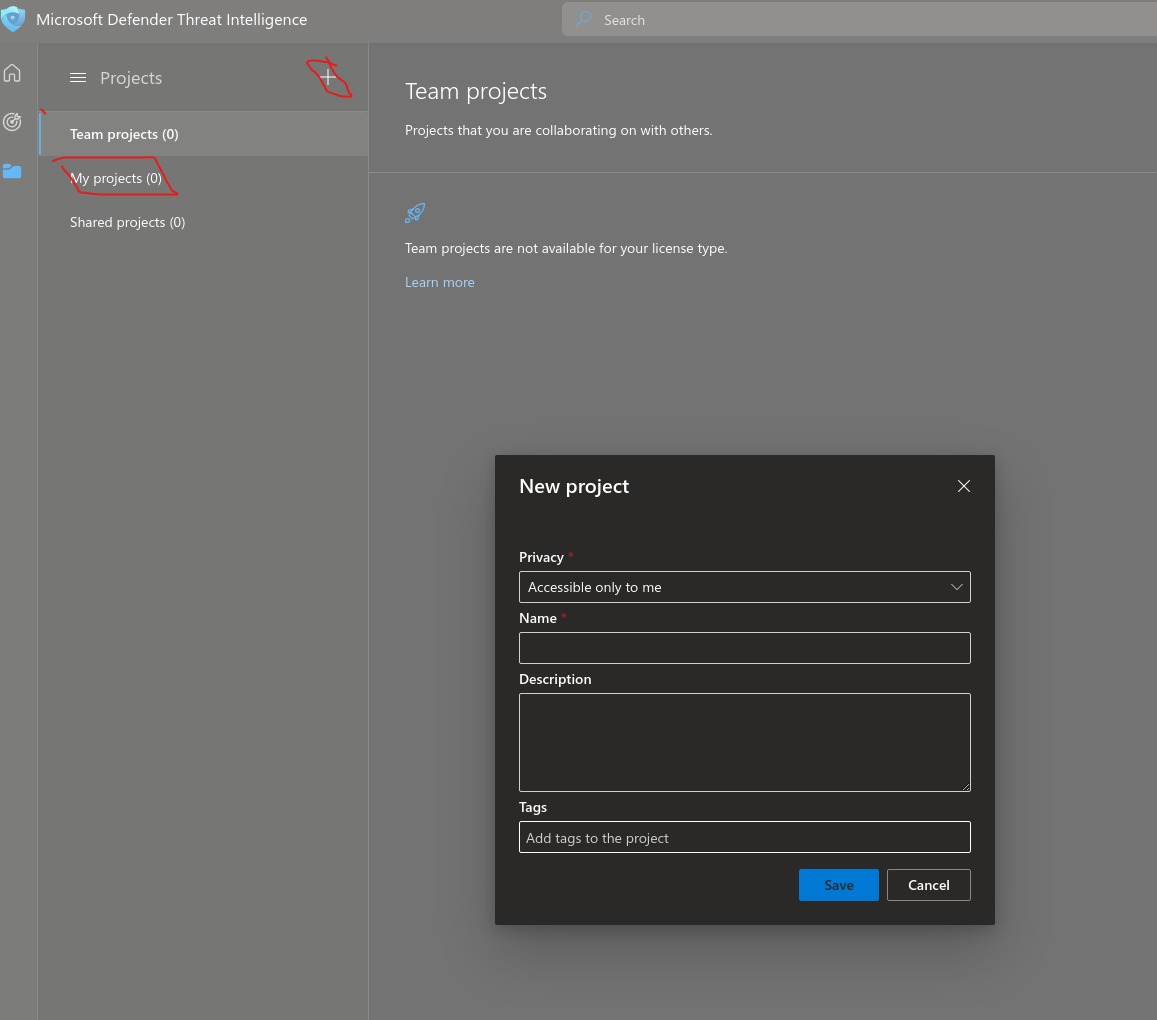
- Creating Teams account and Project. In free license we can’t create Teams account but we can create 1 project with accessibility to ownselves.
- After Project creation, we do have to add artifacts to run the jobs
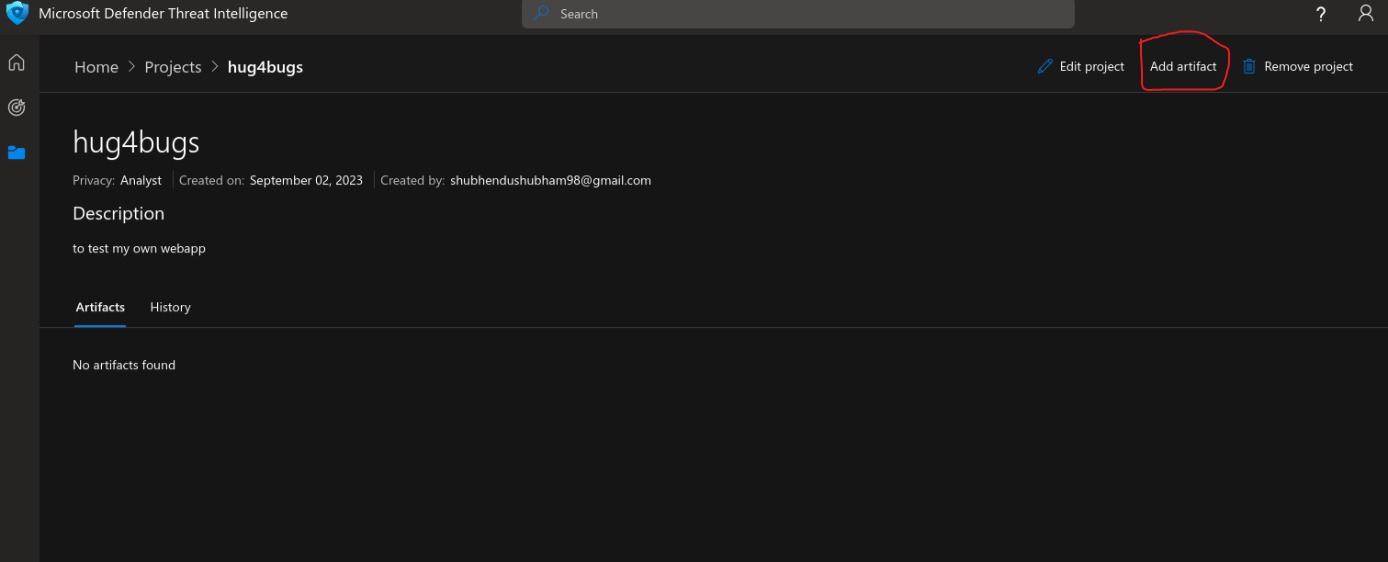
- Artifacts can be either for domain or IP specific
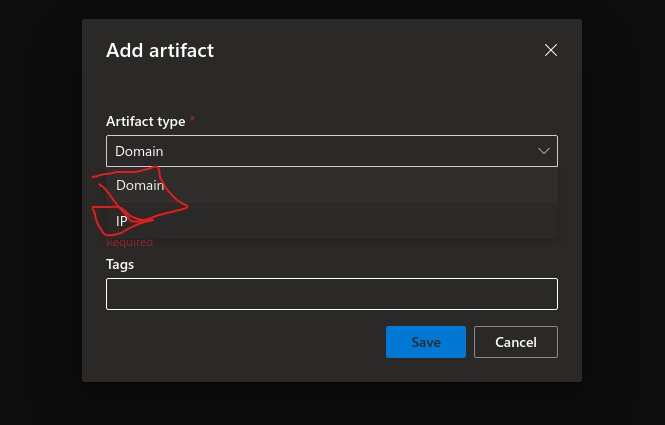
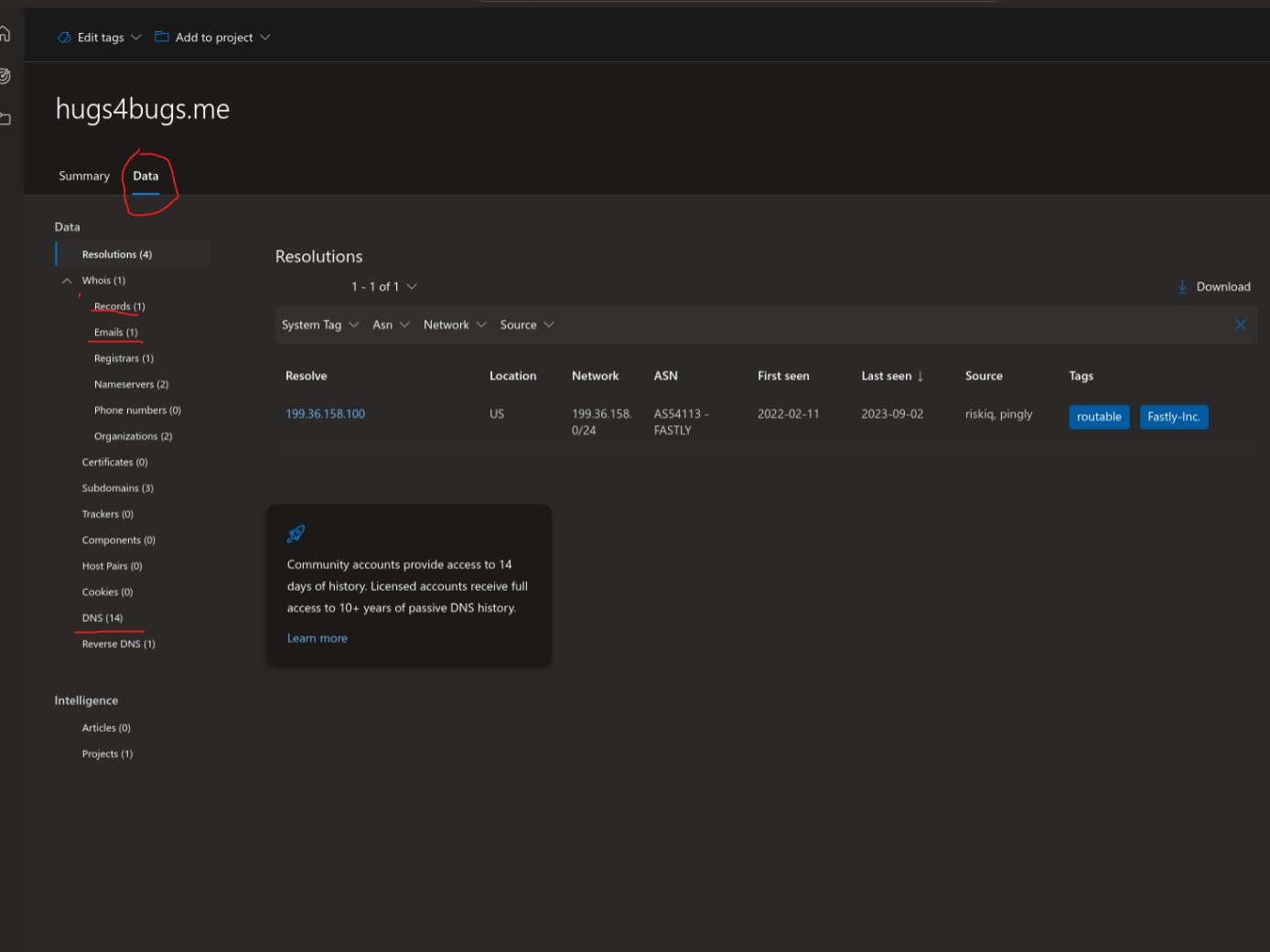
- Run Jobs and It’ll seach from each search type like Tags, components, Trackers, WHOIS, Certificate, Cookies and provides result into two part
- First is summary
- Data Tab which contains all details about scans
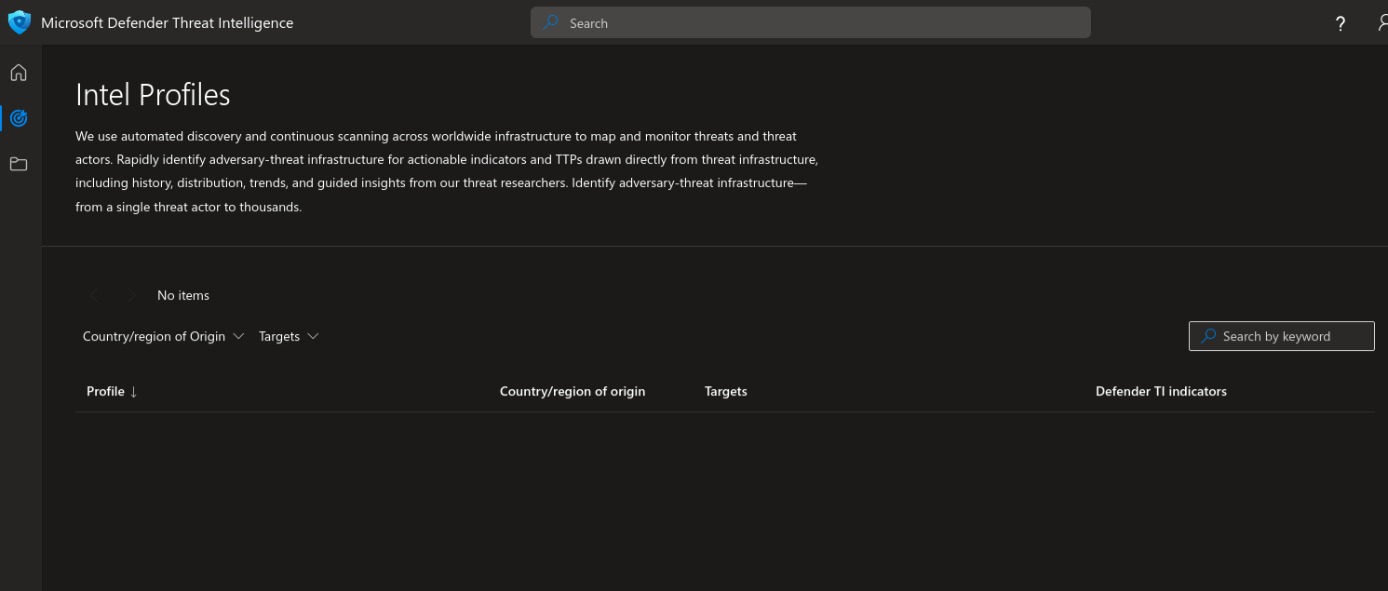
At Intel profile, we can filter out Threat actors and groups by Targets and country

Comments