1 min to read
Automate Multiple Login failure alerts
Reduce SOC analyst burnout

MTTD (Mean Time To Detect) and MTTR (Mean Time To Response/Remediate) are the two crucial factor in Defensive side of hashtag#cybersecurity Major challenge for Blue team is resource burnout and manual investigation on repetitive task which increase average MTTR .
Let’s understand use case to orchestrate security flow use Case :- Automate Multiple login failure alerts response
Workflow link :-
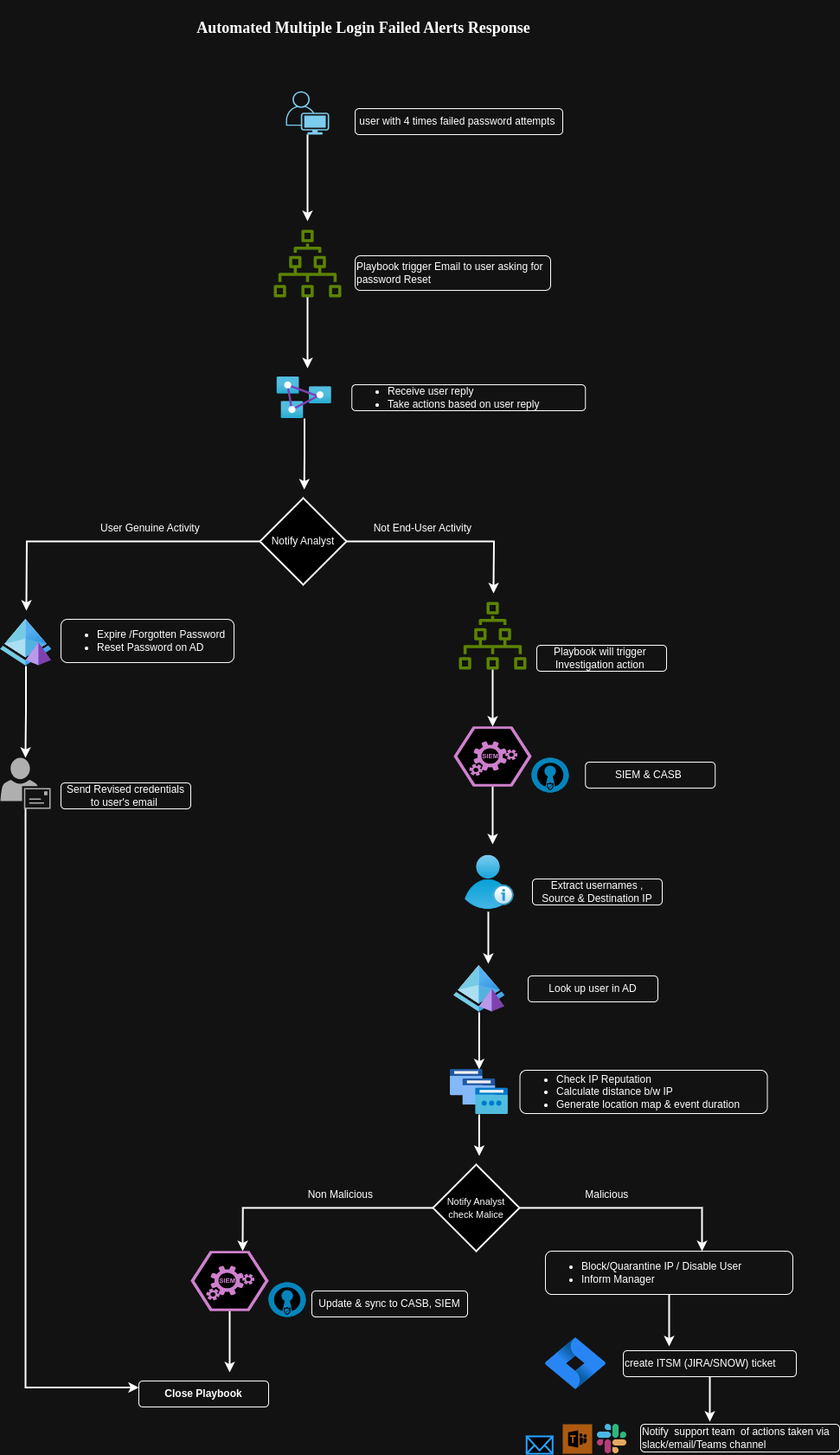
Here we’ll use SOAR (Security Orchestration Autoamtion and Response) to automate Multiple login failure alert response. It can be achived with the both Azure Logic & Power Apps.
Steps:-
- We’ll set threashold of login failure eg- 4/5 times
- When user account have multiple times failed password attemps,
- Playbook will trigger an email to user asking for justification
- Waits for the end user reply & inform analyst
- As soon as it receives response from end user, next job will start based upon reply
- If user confirms genuine activities then look for justification
- In case password expired/forgotten, reset password and share revised login credentials to user over mail
- Incase if failed password attempts are not from end user then playbook will trigger investigation action
- Fetch Incidents details from SIEM and UEBA connectors
- Query will run to extract usernames, Source IP, Destination IP, Assets details
- Cross verify username with existing users list in AD (Active Directory)
- Check IP reputation with multiple open source IP checker. ps :- It can be automated with help of API , eg if we do use VirusTotal then Virus total API can be integrated with SOAR platform ,And in case of Microsoft Azure, Microsoft Threat Intel profile could be linked up or TAXII API
- Check distance between IP in case of multiple location jump and generate location map & event duration
- Notify the analyst with result score
- If activity is malicious then Quarantine?Block IP and user, Create ITSM ticket with defined SOP severity & notify support team via email/Teams channel or slack
- If it’s non malicious then close incident with false positive justification.
- Stop playbook
Keep Learning, Keep Troubleshooting !

Comments