10 min to read
Sentinel Authentication:you're probably doing it wrong?
oauth vs Service Principal vs Managed Identity
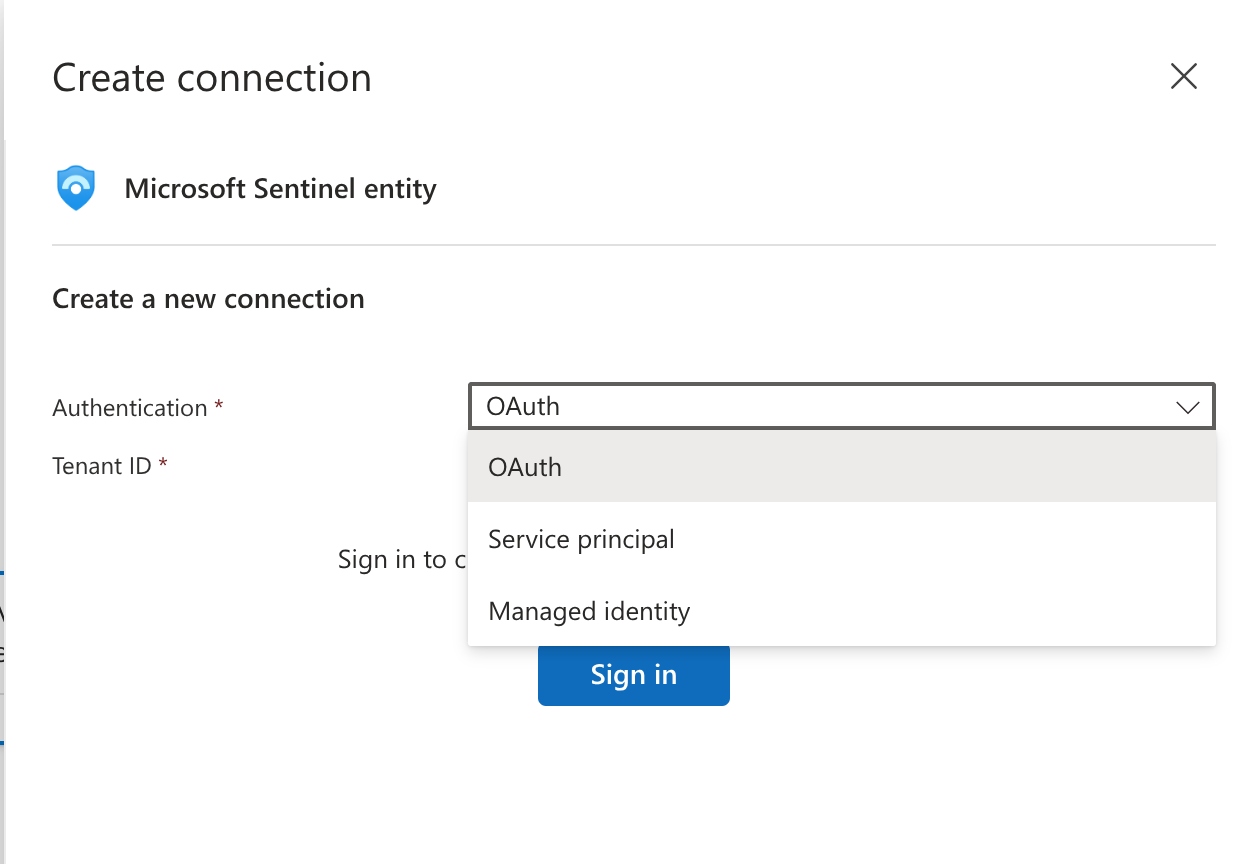
When your Security Operations Center starts automating incident response with Microsoft Sentinel playbooks or SOAR features (via Logic Apps), one question consistently surfaces during architecture reviews: “Which authentication method should we use?” I’ve seen teams default to OAuth because it’s familiar, only to face credential sprawl nightmares six months later. Others jump straight to managed identities without understanding when a service principal actually makes more sense.
Let’s directly jump to the point and talk about three authentication methods available for the Microsoft sentinel Logic Apps connector, when each one fits your security architecture and the operational realities that often get glossed over in documentation.
I mean below pic

Three Authentication Methods
when you create a connection to the Microsoft Sentinel connector in Logic Apps, you’ll see three options as above in pic
- oAuth
- Service Principal
- Managed Identity
Each servers different use cases, and frankly, choosing the wrong one can create security gaps or operational headaches that’ll haunt your team during the next audit.
- oAuth : THe user Account Everyone Recognizes (and Often Misuses)
What It actually is ?
oAuth authentication uses a real user account from your Microsoft Entra ID tenant. When you select this option, you sign in with your credentials and the logic app connection operates under that user’s identity and permissions.
The Good
Speed to Deploy
Your SOC analyst can create a playbook, authenticate with their own account, and have it running it under 10 minutes. No app registrations, no permission requests to the identity team (IAM Ops Team).This makes oAuth perfect for proof-of-concept(PoC) work and initial testing.
Audit Trails when SOC analyst checks sign-in logs, you see actual usernames. Your compliance team understands user accounts. They’ve been auditing them for years.
The Bad( why CISOs should Pay attention)
Here’s where things get messy in production environments :
person leaves, playbook breaks
Let’s understand this with e.g suppose “Shubhendu” is a soc analyst , who built 5 critical incident enrichment playbooks using his oauth connection, Shubhendu accepts a job offer from another company. His account get disabled by IAM or Offboarding HR Team . Now at 3 AM, your playbooks start failing, and nobody knows why until someone remembers “Shubhendu” authenticated them 6 months ago.
Passoword Resets are silient Killers
User changes their password. Multi-factor authentication gets reset. Conditional Access policies change. Any of these can break OAuth connections without warning. The connection requires re-authentication when credentials change, but your playbook doesn’t send an alert when it stops working.
Privilege Creep
To make the playbook work, someone grants the user account Microsoft Sentinel Contributor rights. That person now has those permissions for everything they touch in the console too, not just the automated workflows. This violates least privilege principles and creates separation of duty issues.
shared Accounts are worse
I’ve seen teams create “svc-sentinel-automation@company.com” generic accounts to “solve” the person-leaving problem. Now you’ve got a shared credential, password rotation becomes a coordination nightmare, and you’ve lost individual accountability in your audit logs
When oAuh makes sense?
use oAuth authentication for:
- Development & testing env
- PoC
- Short term tactical automations (<30 days)
- Demo or training
Never use oAuth for production playbooks that need to run unattended for extended periods.
Service Principal: The Traditional Enterprise Approach
What it actually is?
A service principal is created by registering a Microsoft Entra application. It provides an enhanced ability to control permissions, manage credentials, and enable certain limitations on the use of the connector. Think of it as creating a dedicated application identity specifically for your automation.
The Good
Decoupled from humans
The service principal exists independently of any user account. People can leave, get promoted, or move to different teams without impacting your automation. This solves the biggest operational problem with OAuth.
Explicit credential management.
You control when credentials are created, where they’re stored (ideally Azure Key Vault), and when they expire. During your annual security review, you know exactly which secrets/ certificates need rotation.
Granular permission control.
You can assign the service principal only the specific Sentinel roles it needs. It has zero console access. It can’t accidentally (or maliciously) do anything outside the playbook’s intended scope.
Multi-environment flexibility.
Need the same automation logic across dev, test, and prod? Create separate service principals for each environment with different permission levels. Your dev playbooks can’t accidentally modify production incidents
Cross-tenant scenarios.
If you’re a managed security service provider or have multiple Sentinel workspaces across different tenants, service principals can be configured for multi-tenant access. Managed identities can’t do this.
The Bad: The Operational Overhead
Secret rotation is your responsibility. Azure requires secret rotation every two years, but best practice is more frequent like 90 days . Miss a rotation deadline? Your playbook breaks at 2 AM on a Sunday. You need a process, calendar reminders, and someone who owns this task.
Initial setup friction. Creating a service principal requires registering an application in Entra ID, generating a client secret, documenting the Client ID and Tenant ID, and coordinating with your identity team if you don’t have appropriate permissions. It’s not hard, but it’s more steps than clicking “Sign in.”
Secret storage complexity. That client secret can’t live in plain text in documentation or code. You need Azure Key Vault or similar secure storage, which means additional dependencies and access controls.
Audit trail requires context. Your sign-in logs show a service principal GUID, not “Shubhendu’s playbook for phishing response.” Service principal sign-ins are logged in AADServicePrincipalSignInLogs. You need good naming conventions and documentation to understand what’s doing what during an incident.
When Service Principal Makes Sense
Use service principal authentication for:
- Production playbooks with moderate complexity (10-50 playbooks)
- Cross-tenant or multi-workspace scenarios
- Environments where you have established secret rotation processes
- Scenarios requiring explicit credential backup and disaster recovery
- When you need portability (exporting and importing playbooks with the same identity across different Azure regions)
- Legacy automation migrating from older patterns where your team is already comfortable managing app registrations
Managed Identity: The Modern, Secure Default
What it actually is?
Managed identity allows you to give permissions directly to the playbook, which is a Logic App workflow resource. The connector actions operate on the playbook’s behalf, as if it were an independent object with its own permissions. Azure automatically creates and manages the identity lifecycle.
Why Security Architects Love It
Zero credential management. Managed identities eliminate the need for users to manage credentials by providing an identity for the Azure resource and using it to obtain Azure Active Directory tokens. No secrets to rotate, no passwords to expire, no Key Vault dependencies for credential storage. Azure handles everything behind the scenes.
True least privilege. You assign permissions directly to the playbook resource. This specific Logic App can update Sentinel incidents. That’s it. Not the person who created it, not some shared service account, just this one automation workflow.
Automatic lifecycle management. By using a managed identity, the Logic App creates an enterprise application itself and manages the secrets itself. When you delete the Logic App, the identity goes away. No orphaned service principals cluttering your Entra ID after you decommission old playbooks.
Audit clarity. Managed identity sign-ins are logged in AADManagedIdentitySignInLogs. The logs clearly show which playbook resource performed which action. During a security investigation, you can trace activity back to specific automation workflows, not generic application IDs.
The Limitations (they’re minimal)
-
Single tenant only: Managed identities are scoped to Azure resources. If you need your playbook to access Sentinel in a different tenant, managed identity won’t work. You’ll need a service principal
-
Resource dependency: The identity is bound to the Logic App resource. If you need to export a playbook and deploy it elsewhere (different subscription, different region, DR scenario), you’ll need to reconfigure permissions in the destination. Service principals offer more portability.
-
Connector support gaps: Most Azure-native connectors(content Hub) now support managed identities, but some third-party or legacy APIs still don’t. In those cases, you may need a Service Principal or OAuth fallback.
When Managed Identity Is The Right Choice
- All new production playbooks (this is now Microsoft’s recommended default)
- Single-tenant Sentinel deployments
- High-volume automation (50+ playbooks) where secret rotation overhead becomes unsustainable
- Security-first environments where eliminating credential exposure is a top priority
- Teams without mature secret management practices who want to avoid the operational overhead
- Organizations following Zero Trust architecture where managed identities align with Microsoft’s security guidance
Decision Framework: What Should You Choose?
Here’s how I advise security architects and SOC leaders to make this decision:
-
Start Here: Default to Managed Identity Unless you have a specific reason not to, use managed identity for production playbooks. Always prefer managed identities over service principals.security benefits, operational simplicity, and Microsoft’s official support make this the clear default choice for same-tenant automation.
-
Exception 1: Multi-Tenant Requirements
If you need cross-tenant automation (MSSP scenarios, complex holding company structures, disaster recovery across tenants), use service principals. Managed identity simply doesn’t support this architecture
- Exception 2: Portability and Disaster Recovery Requirements
If your risk management team requires the ability to export playbooks and immediately deploy them to a different Azure region or subscription without reconfiguration, use service principals. The credential portability matters more than automatic credential management. That said, evaluate whether this requirement is still valid—many organizations find that managed identities with infrastructure-as-code deployment patterns actually work better for DR scenarios.
- Exception 3: Legacy Constraints
If your organization has dependencies on existing automation tooling or deployment pipelines that are tightly coupled to service principals, you may need to continue using them short-term. However, build a migration roadmap. Now that managed identity is GA, there’s no longer a technical or support reason to avoid it. The operational overhead and security risks of service principals don’t justify permanent use when managed identity is available.
Never Use OAuth in Production
Seriously. OAuth authentication with user accounts has no place in production Sentinel automation that needs to run unattended. The person-dependency risk is too high. Use it for dev and test only.
Implementation Best Practices
For Managed Identity
- Enable system-assigned identity on your Logic App first before creating any connector connections
- Assign minimum required Sentinel roles (Reader for data retrieval, Responder for incident updates, Contributor only if necessary)
- Use consistent naming conventions for playbooks so audit logs make sense (“incident-enrichment-ip-reputation”, not “LogicApp-12345”)
- Document dependencies in your runbooks. If a managed identity playbook calls Azure Functions or other resources, document those permission requirements
- Test identity removal in dev environments. Verify playbooks fail gracefully when permissions are revoked
For Service Principal
- Use Azure Key Vault to store client secrets. Never hardcode credentials or store them in documentation set calendar reminders for secret rotation at least 30 days before expiration
- Name service principals clearly (“sp-sentinel-prod-incident-enrichment”, not “app-registration-001”)
- Assign minimum required API permissions in the app registration, not just Sentinel roles
- Enable secret version tracking in Key Vault so you can rollback if a new secret causes issues
- Implement monitoring for failed service principal sign-ins (this is your early warning for expired secrets)
For OAuth (Dev/Test Only)
- Use dedicated test user accounts, not personal SOC analyst accounts
- Set automatic expiration policies on OAuth connections (force re-authentication every 90 days to prevent forgotten dev playbooks from accumulating stale permissions)
- Never grant permanent Contributor roles to users who authenticate dev playbooks. Use time-limited PIM activation instead
- Tag all OAuth-authenticated Logic Apps so you can identify them during production deployment reviews


Comments