6 min to read
Blue Team vs Red Team
Two sides of a coin!

Hold on, before I start lemme clear it those teams are called Blue and Red not because they hold Blue or Red colour uniforms….
Jokes apart
Let’s start, in the ocean of Cybersecurity Information Security plays an important role.And officially we do divide Infosec teams into 2 category i.e Blue Teaming and Red Teaming
Blue Team
They are the boarder Security force for any organisation. They act like defender,responsible for establishing a defense mechanism for any corporate environment or infrastructure.
When an attacker, or Red Team guys try to break down into system and gain access, blue teams put their efforts into placing necessary and optimized controls to make their organization safe. Due to the increase in cyber threats, blue teams are necessary need for any organization now.
Work Cult
Blue teams don’t any generic methods to guard an organization. However, they have various tasks, which further have well-crafted ways that can be used to achieve particular aims. Blue Team tasks may include but not limited to below:
A blue team performs all of the security operation center (SOC) functions and is responsible for SIEM, incident handling and response, packet analysis, vulnerability scans, and threat intelligence.
Risk Assessment
Defenders (Blue Team) map the entire corporate environment in accordance with well-known security standards like ISO27001:2013, PCI, NIST, etc., in this exercise.and look into the cracks in their surroundings.Any risks that could hinder the company’s operations, either directly or indirectly, are included in this assessment.To begin, we conduct the GAP Analysis in accordance with established IT security standards.After identifying the Information Security gaps, we examine the risks associated with those gaps. We accept some risks that we believe should not be prioritized and reduce others by implementing the recommended controls as suggested by the framework.for such risks for which we are unable to implement the framework’s recommended controls.In an effort to reduce risks, we push some compensating controls.
Incident Response Plan
An Incident Response plan is a set of well-documented steps and procedures that needs to be followed in case of any data breaches or cyber incident. We’ll discuss briefly what these steps are and how we can follow them in case of an unfortunate cyber attack:
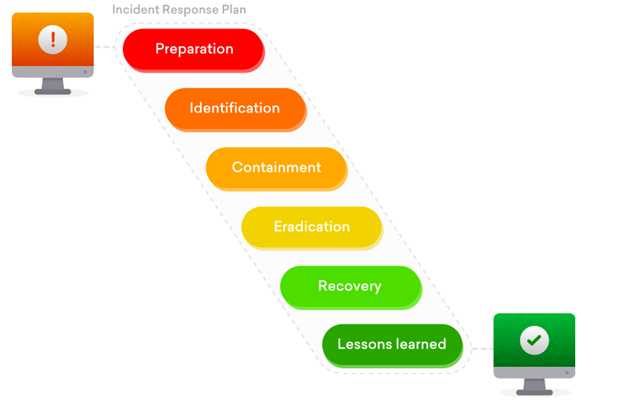
Preparation
We must ensure that our employees are aware of their roles and responsibilities in cyber attacks during the preparation phase.When there is a cybersecurity incident, we need to make sure that the steps are well documented and followed. Additionally, we must conduct incident response drills on an annual, if not biannual, basis.
Identification This step is responsible for identifying a security incident. Various questions need to be answered before completing it:
a) What is the timeline of incident? b) How was it identified? c) Who identified it? d) What was the scope of the compromise?
Containment
During this phase, we have established whether or not the security breach has occurred.In such high-stress situations, our first instinct will be to get rid of the incident and all malicious activities.
But this may lead to severe consequences, which may lead to clear out the malicious activity properly. So, rather than this approach, we tend to contain the malware in a restricted environment and analyze its behavior. In this way, we know how the malware is behaving and how it is improvising w.r.t the target environment.
Eradication
Eradication In the beginning, we look at the malware and gather the necessary information from this security incident.The next step is to remove any malware or backdoors that may have been introduced into our environment as a result of this incident.
Recovery
This is the method for reintroducing affected devices into your business environment.It is essential to return your business activities and frameworks to full operation immediately during this time.
Vulnerability and Patch Management
During this phase, we evaluate our infrastructure-based assets on a biannual, if not quarterly, basis for potential vulnerabilities.However, a documented Vulnerability and Patch Management procedure is necessary due to the frequent emergence of new exploits and vulnerabilities.
This includes going through each and every inventory.We can perform this activity in a sample to get a basic idea of our ecosystem’s health if the scope is too broad.
Our patch management efforts must take precedence once we have completed inventory vulnerability scanning.We are unable to begin patching servers that are neither publicly accessible nor business-critical.To ensure that high-priority assets are addressed first, we must prioritize our efforts.
RED TEAM
A Red team consists of individuals who attempt to circumvent all of an organization’s security controls by impersonating adversaries.They look at the environment, create attack surfaces that are unique to an organization, and then objectively evaluate all of the security controls that are in place, whether they are physical or logical controls.
They are also known as Ethical Hacker
They frequently use known vulnerabilities, security misconfigurations, zero-day exploits, and a “hacker” mindset to circumvent the existing access controls, authorization controls, physical security, and other security measures.They will take into account every possible route that could compromise an organization.
Team Cult
The operations of a red team are comparable to those of a sophisticated adversary.To successfully attack a target, they will adhere to a set of instructions.The following steps from Fire Eye’s methodology are made crystal clear below Red Team:
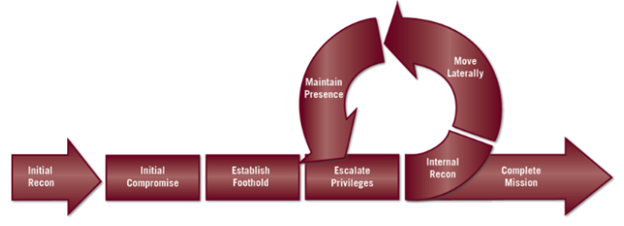
A red team looks to exploit the following:
Penetration Testing:
It is a security posture assessment of the host, network, and applications.The assessor tries to get deep into the target’s scope, act like a malicious actor, and violate the engagement rules by abusing the target environment.
-
Known vulnerabilities
- Wireless access
- Physical security breach
- Active directory exploits
- File servers
- Endpoints
- Ports
The red team follows every step of the cyber kill chain just like a hacker would. Here are a few of the tools used by the Red Team:
Reconnaissance
- Nikto
- Sqlmap
- Nmap
Weaponization
- Social engineering
- Metasploit
Command & Control
- Cobalt strike
- DNSExfiltrator
- Powershell-RAT
Privilege Escalation
- Mimikatz
Now summarize all into tabular format
| Red Team | Blue Team |
|---|---|
| Offensive Security | Defensive Security |
| Eithical Hacking | Infra Protection |
| Exploiting Vulnerabilities | Damage Control |
| Penetration Test | Incidents Response |
| Black Box Testing | Operational Security |
| Social Engineering | Threat Hunters |
| Web App Scanning | Digital Forensics |
Thanks for reading, Keep learning, Keep Troubleshooting


Comments