2 min to read
Build Your Own IOC Playground with ELastic SIEM
Hunt IOC
When it comes to proactive approach of security, threat Hunting comes to the picture. And being aware of IOC aka Indicators of Compromise gives an extra leverage to find malicious urls, hash, IP and block those and take proper action. In this lab, I’m gonna build homelab with Elastic Cloud and Elastic SIEM deployment and generate IOC with AbuseCH .
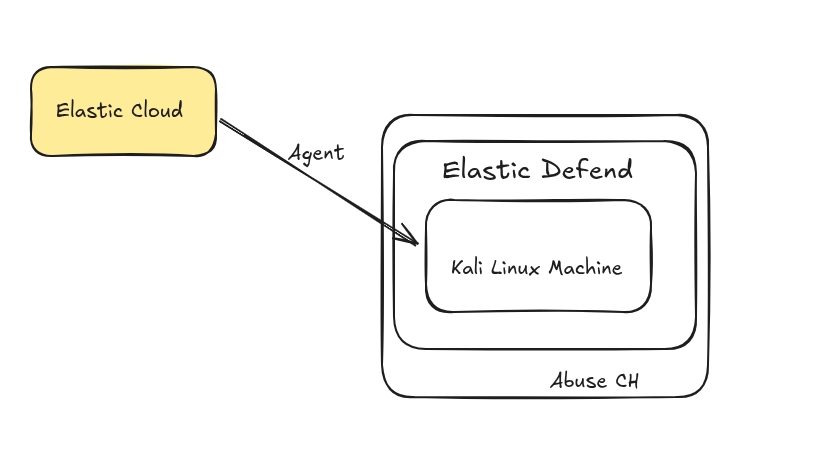
Basic HLD
Steps to create a hosted Deployment
- Signup to Elastic Cloud
- Click on Add Deployment
- Launching Deployement
- Incoming Data Confirmation

Agent Installation
-
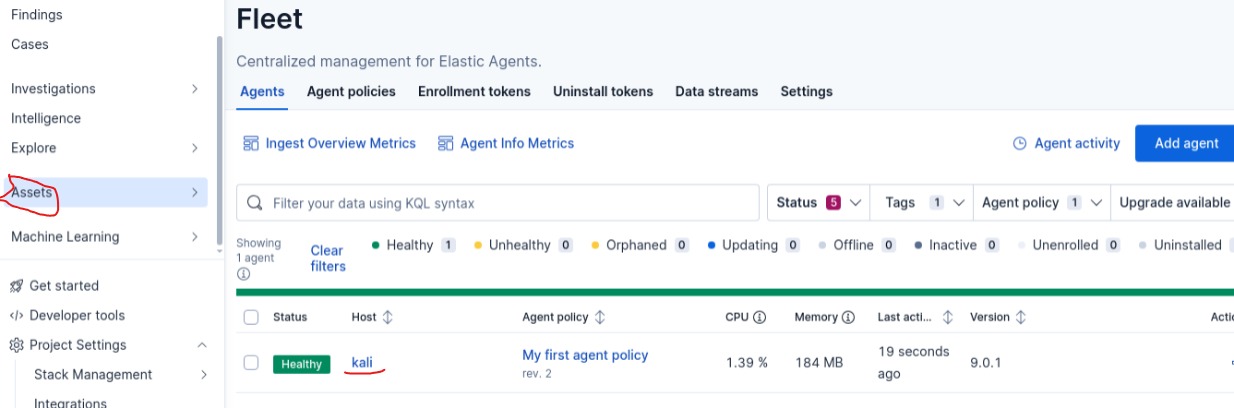
Click on the assets, and Add Agent button

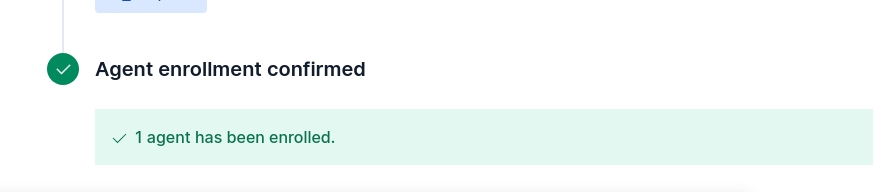
- Enroll in Fleet which means elastic agents in fleet to automatically deploy updates and centrally manage the agent.
- Install Elastic agent on the host machine, in my case it’s Kali Linux Machine
curl -L -O https://artifacts.elastic.co/downloads/beats/elastic-agent/elastic-agent-9.0.1-linux-arm64.tar.gz tar xzvf elastic-agent-9.0.1-linux-arm64.tar.gz cd elastic-agent-9.0.1-linux-arm64 sudo ./elastic-agent install --url=https://a097fdb86de9432ebec921c664a65f9d.fleet.us-east-1.aws.elastic.cloud:443 --enrollment-token=R0FzLTRwWUJtSzFxcVVmU2tyUUo6OUlIdGticVFtcjJhRVNjR2t1NUY4dw==
- Incoming Data confirmation
Now Deploy Elastic Defend
Go to the integration and select Elastic Defend then click Add Elastic Defend
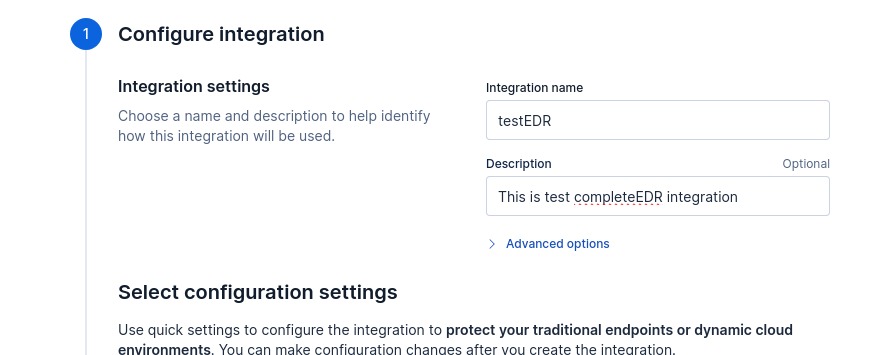
- Configuration Integration give it a name and Description
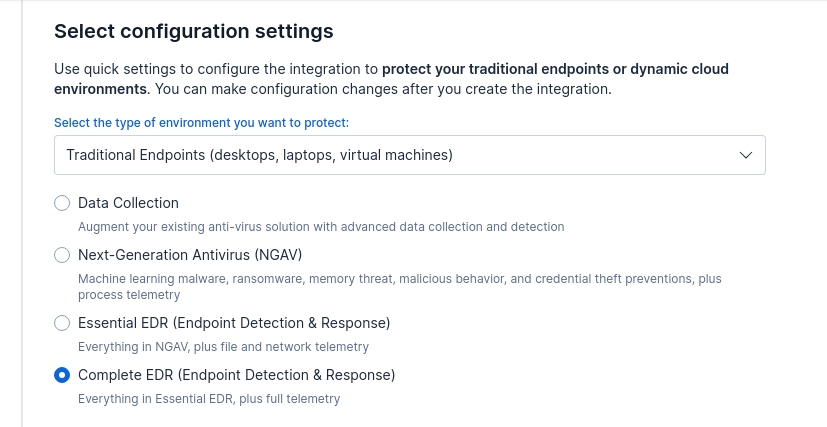
- Under Configuration Settings, it should be “Complete EDR with full telemetry”
- under Where to host section, select existing host and pick same host where we had deployed 1st agent policy
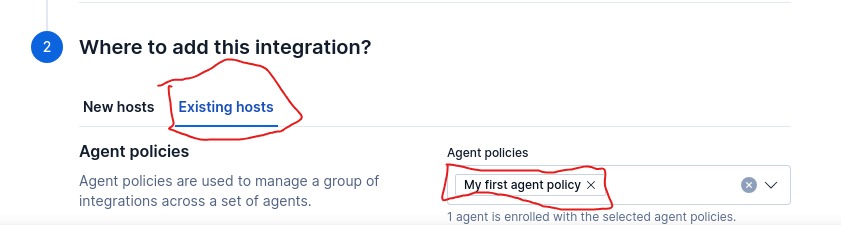
Save & Continue
Now configure Threat Intel feed, from security project left hand menu side click on Intelligence
- Click on AbuseCH TI tool
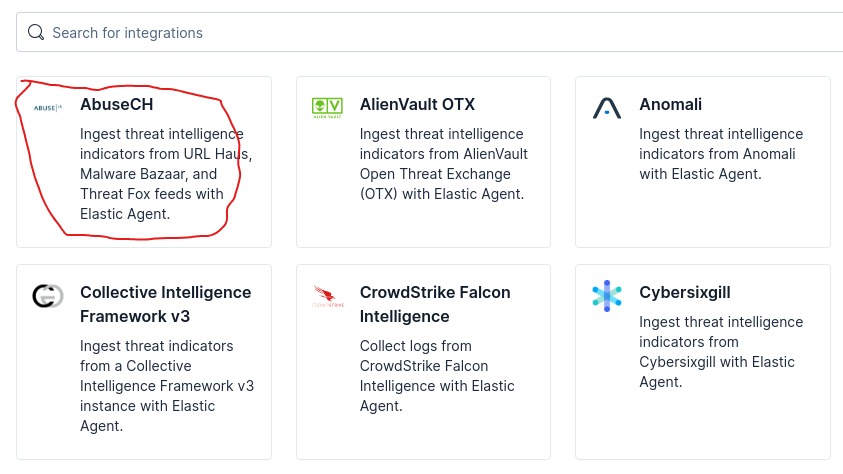
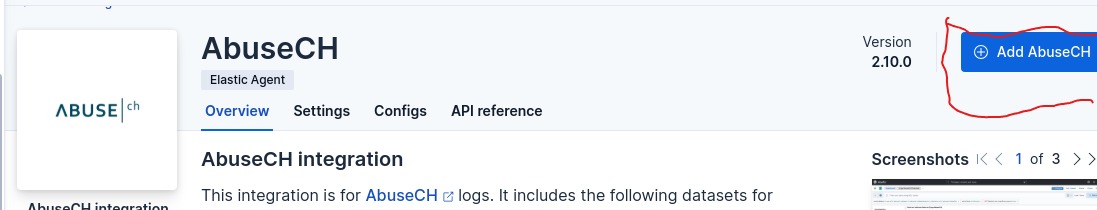
- Add AbuseCH
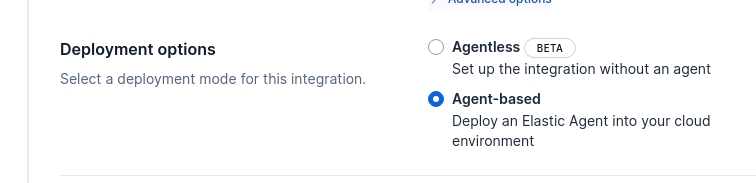
- Select Deployment option as Agent based and toggle off for “collect AbuseCh logs via API using Elastic Agents” . If you have AbuseCH API key feel free to use this option
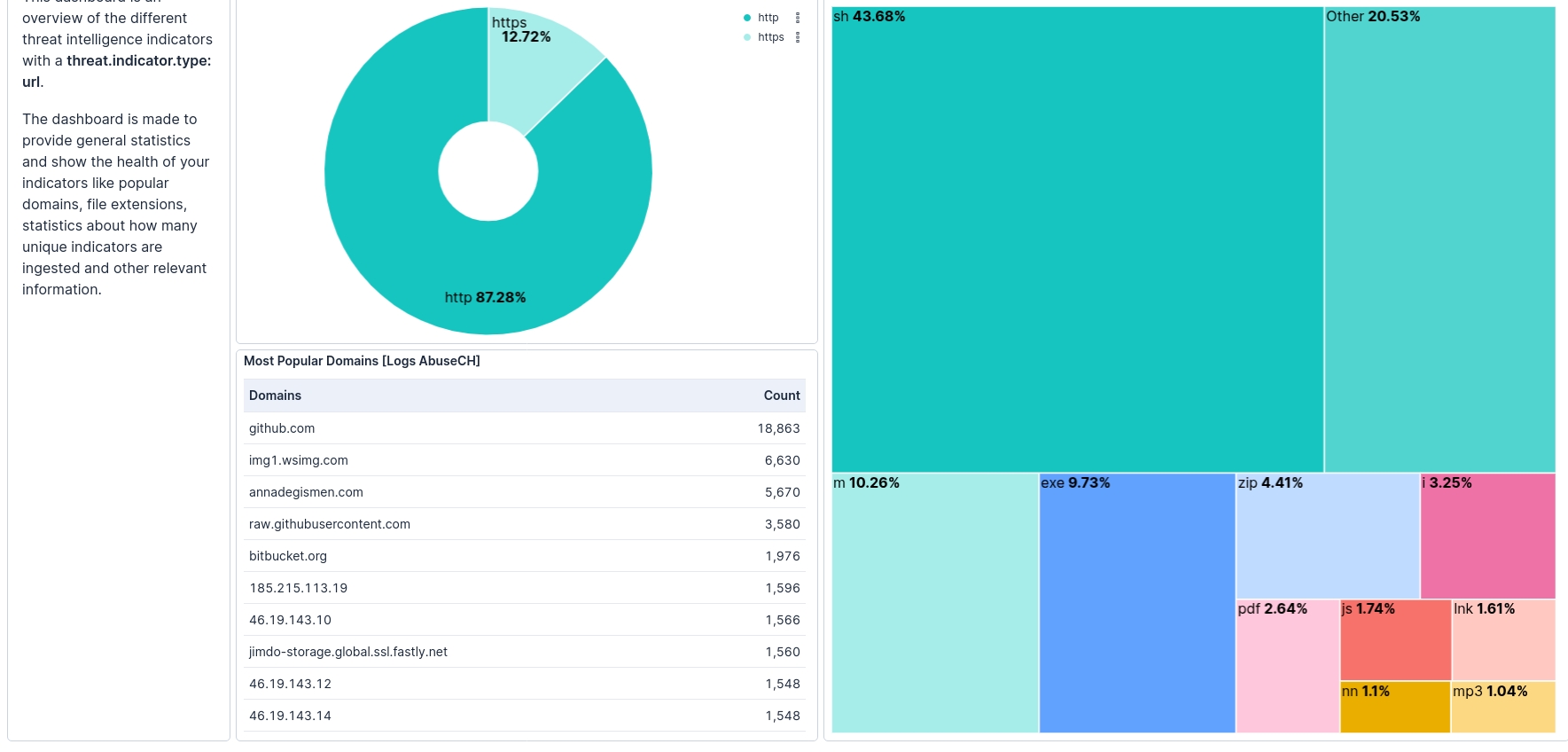
- Now check the TI feeds from Intelligence pannel and feel free to build custom dashboard as well.
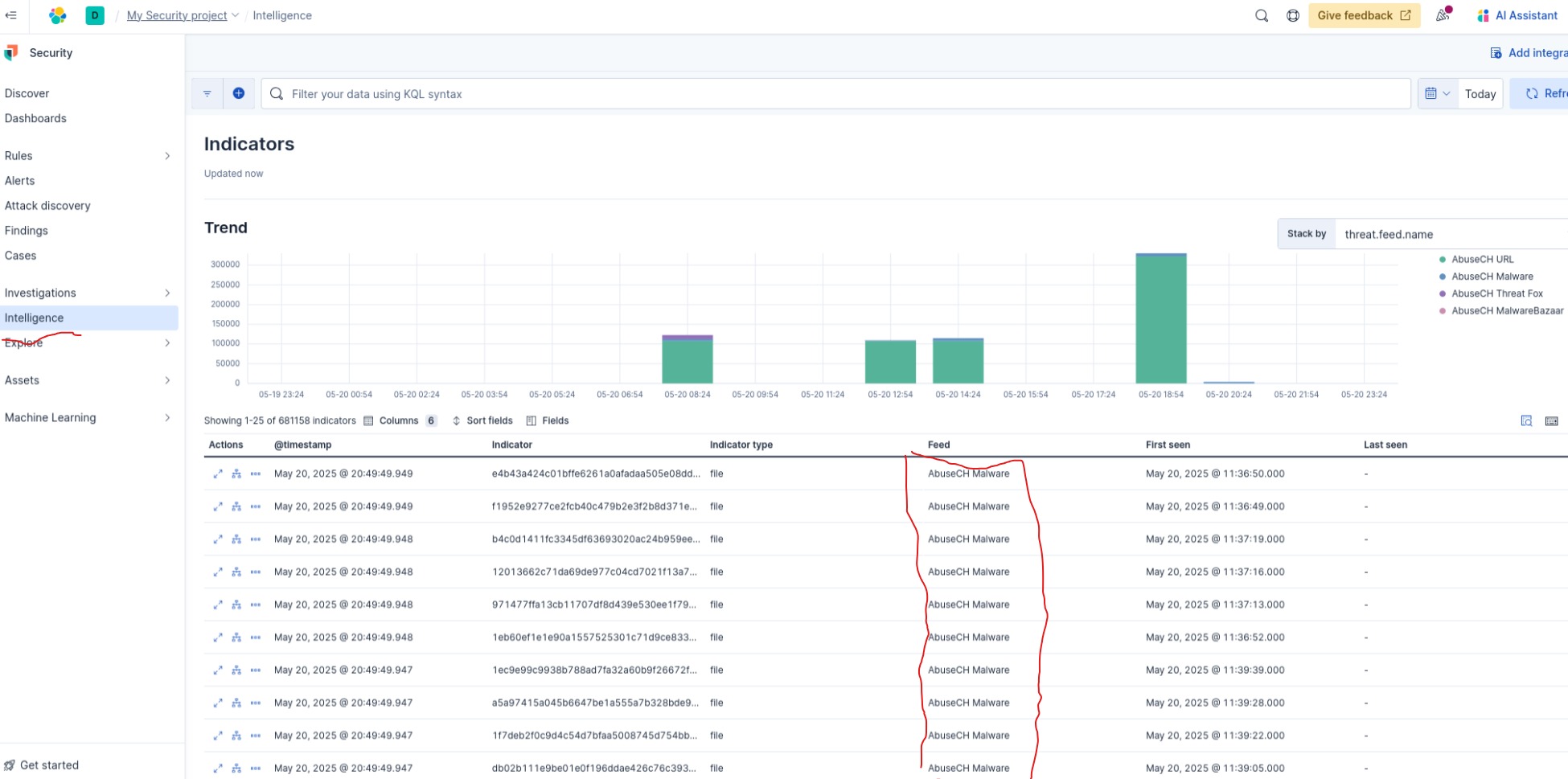
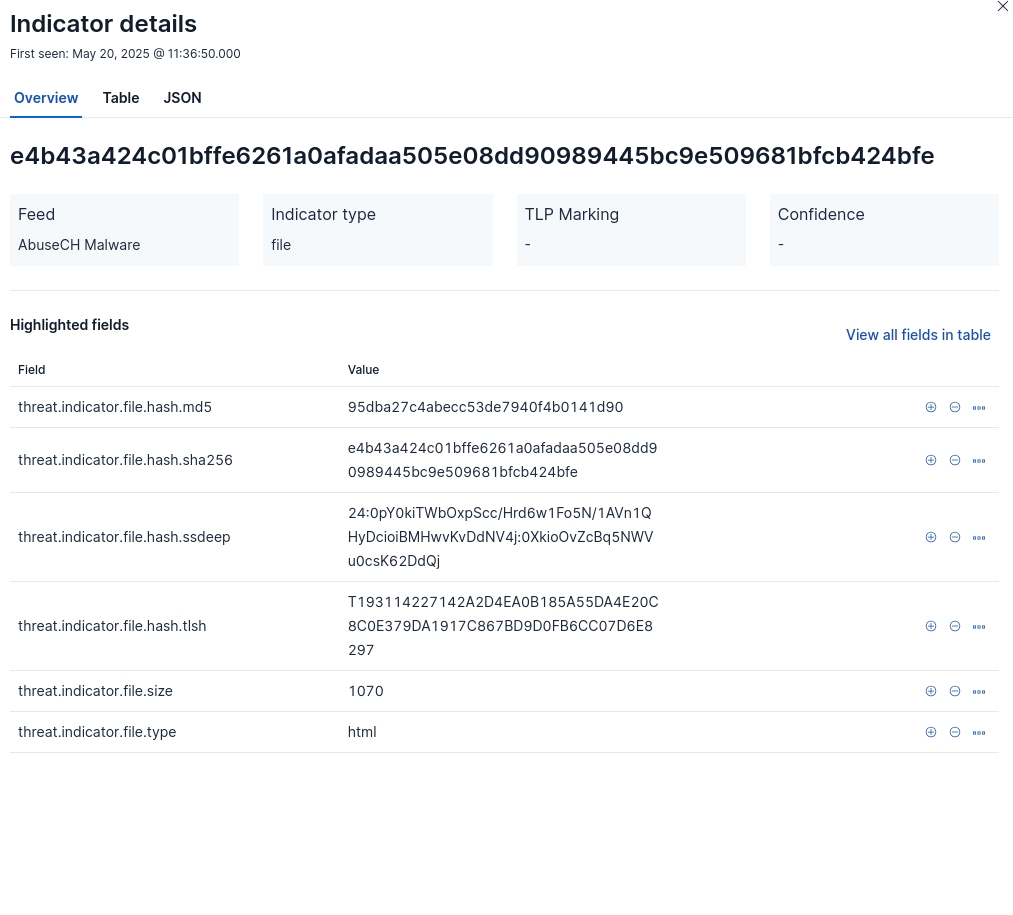
IOC Details
Custom Dashboards

In next part we’ll discuss how to create correlation rule with TI feeds.

Comments