5 min to read
Managing and Storing Secrets:Azure Vault.🙆
Hiding:The Secrets

As we deploy our production to the cloud, we need to be very consious about the sensitive informations eg:- passwords,encryption keys and certificates, which needs to be available to function. Apart from authorised use case, one should take care for unauthorised access.
Hence, comes the Azure Key Vault
What is Azure key vault?
Azure Key Vault is a centrilized cloud service for securely storing and accessing secrets.Hold on what does Secret means? it could be anythings that one want to tightly control access to eg- API keys, passwords, certificates.
Key value services supports 2 types of containers:-
- Vaults : Support storing software and HSM-backed keys,secrets and certificates.
- Managed Hardware Security Modules (HSM) pool : Only supports HSM-backed keys.
Features of Azure Vault :-
-
Manage Secrets
Azure Vault is used to store and tightly control access to tokens, passwords, certificates, API keys etc.
-
Manage Encryption Key :-
It can be used as a key management solution, key vault makes it easier to create and control the encryption keys that are used to encrypt your data.
-
Manage SSL/TLS certificates :-
Key vault enables you to provide,manage and deploy your public and private Secure Sockets layer/Transport Layer Security (SSL/TLS) certificates for both our Azure resources and your internal resources.
-
Store secrets backed by hardware security modules (HSMs) :-
These secrets and keys can be protected either by software or by FIPS 140-2 level 2 validated HSMs.
Benifits of Azure Key Vault :-
-
Centralized application secrets
-
Securely stored secrets and keys
-
Access monitoring and Access control
-
Simplified administration of Application secrets
-
Integration with other Azure services
Hands on
Let’s learn how to add password to Azure Key Vault. Password falls under the category of sesitive information
Ways to add secrets to and read secrets from Key Vault.
- Using Azure Portal
- Azure CLI
- Azure Powershell
Azure CLI is a way to work with Azure resources from the command line or from scripts.
Cloud Shell is a browser-based shell experience to manage and develop Azure resources.An interactive shell that runs in the cloud.
Creating a Key Vault :-
Steps :-
- Go to the Azure portal.
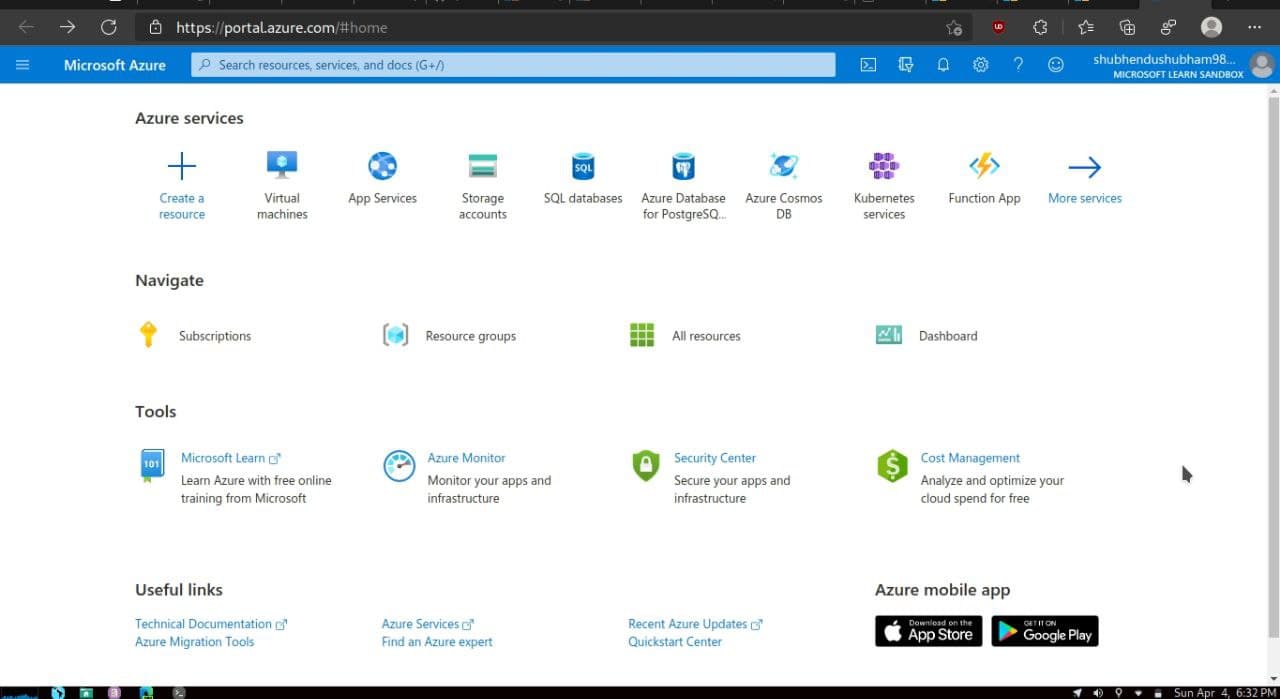
- Select Create a resource under Azure services. This Create a resource pane appears.
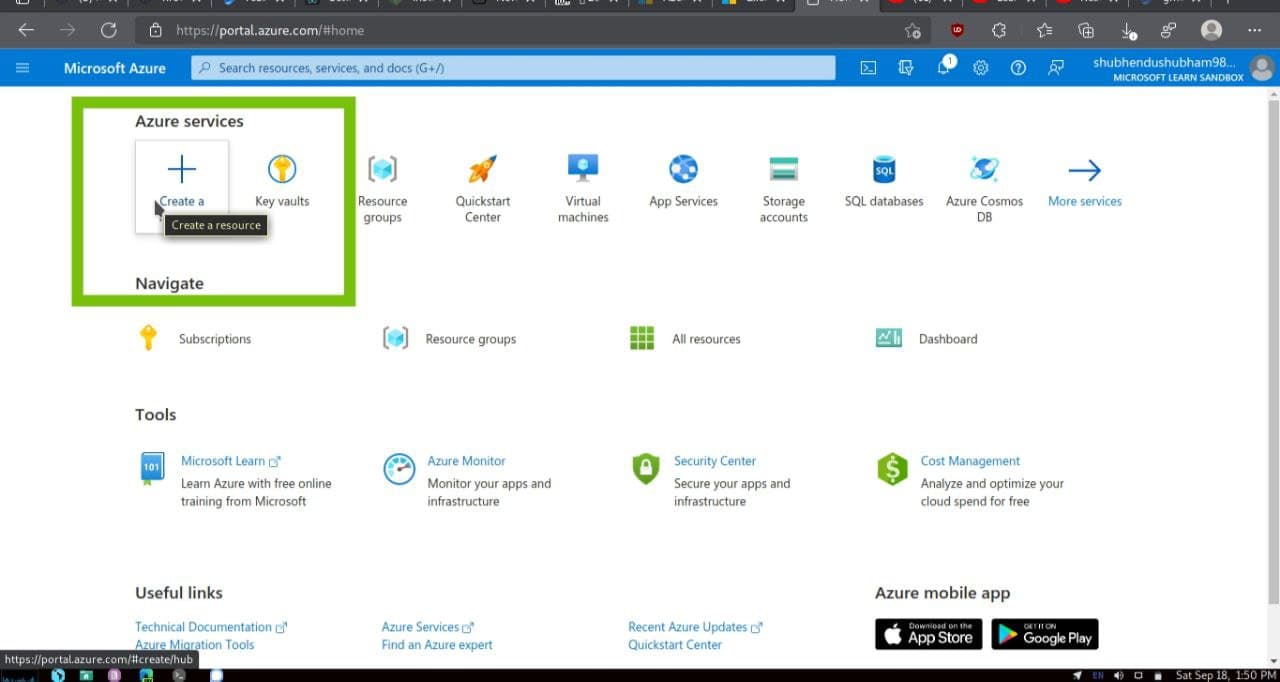
- In the search bar, enter key vault,and then select Key Vault from the results.This will appear Key Vault pane.
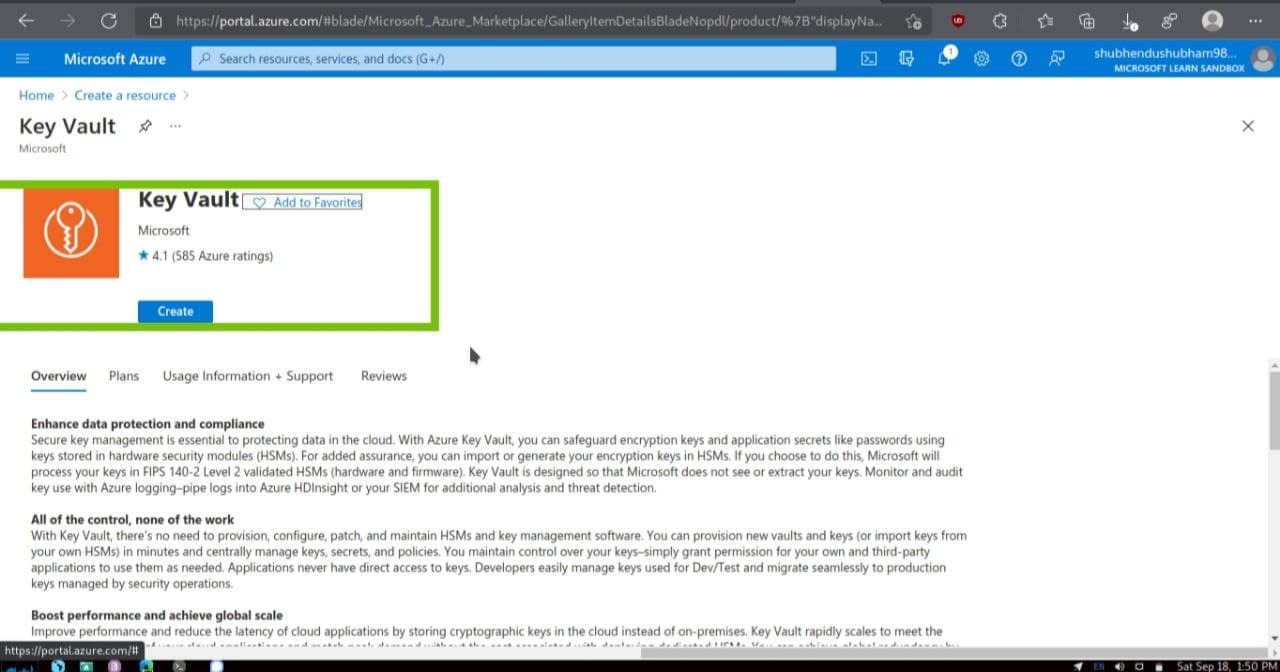
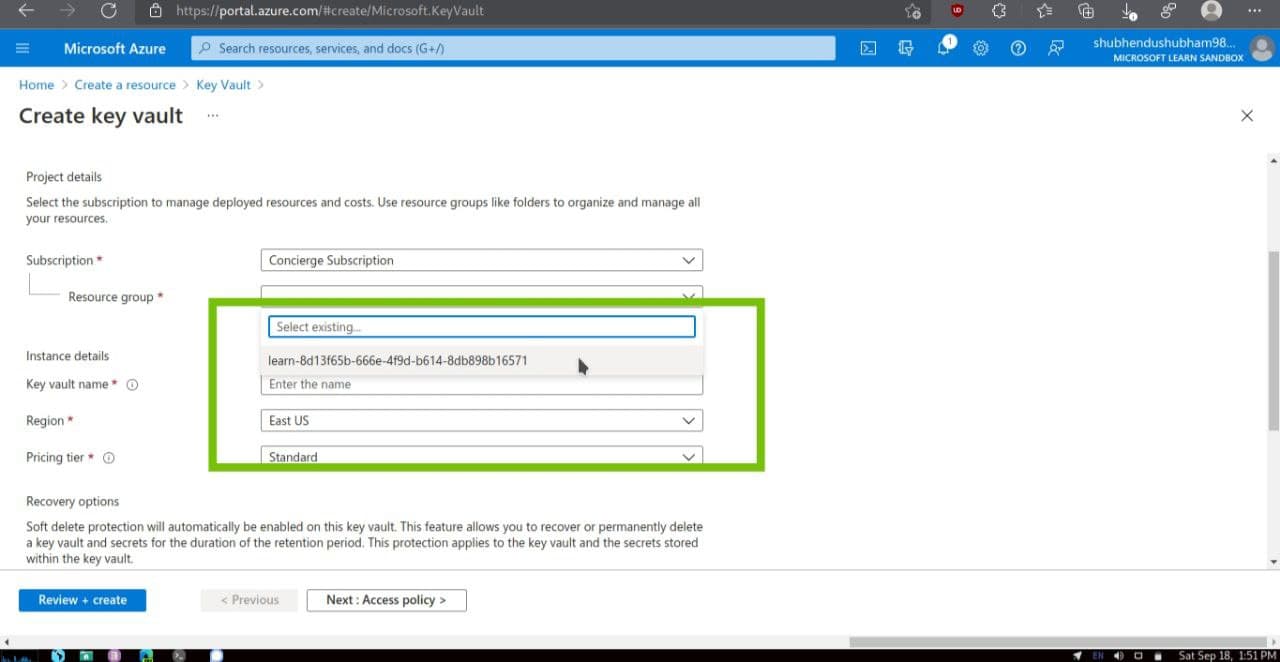
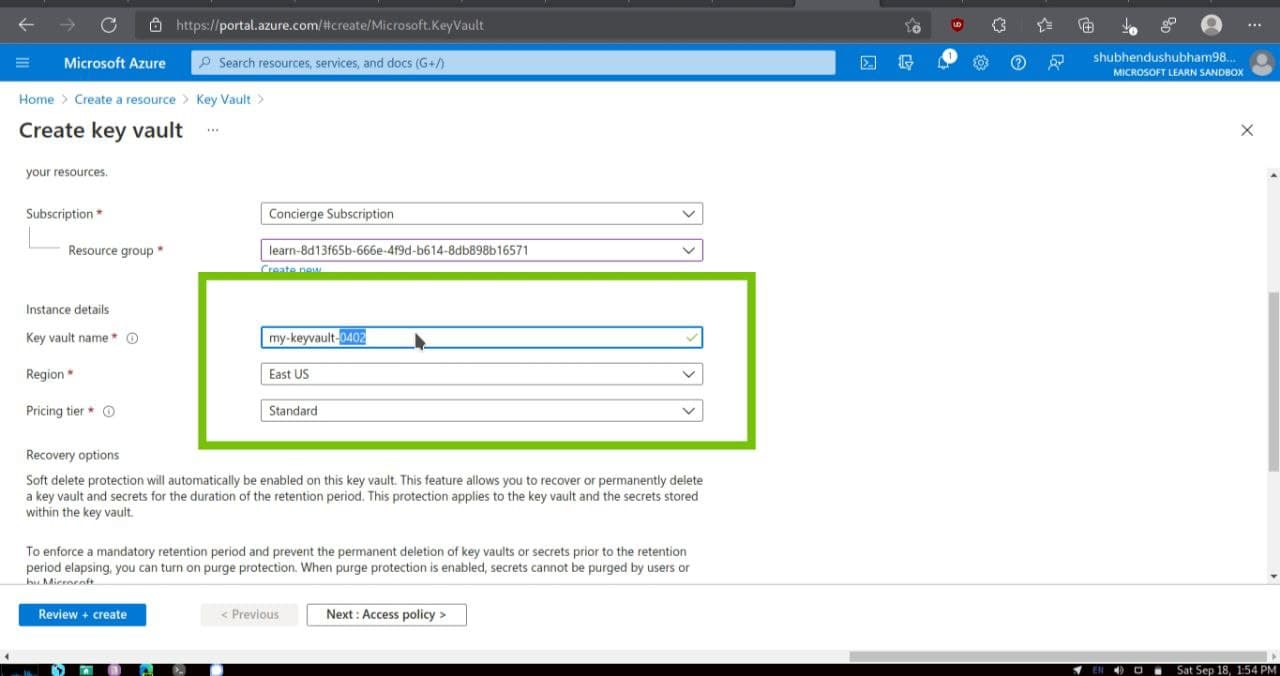
- Click on the Create and fill these following details. Don’t forget to replace NNN with a series of numbers.This helps ensure that the name of your key vault is Unique.
| Settings | Value |
|---|---|
| Project Details | |
| Subscription | Concierge Subscription |
| Resource group | [sandbox resource group name] |
| Instance details | |
| Key vault name | my-keyvault-NNN where NNN is a unique identifier |
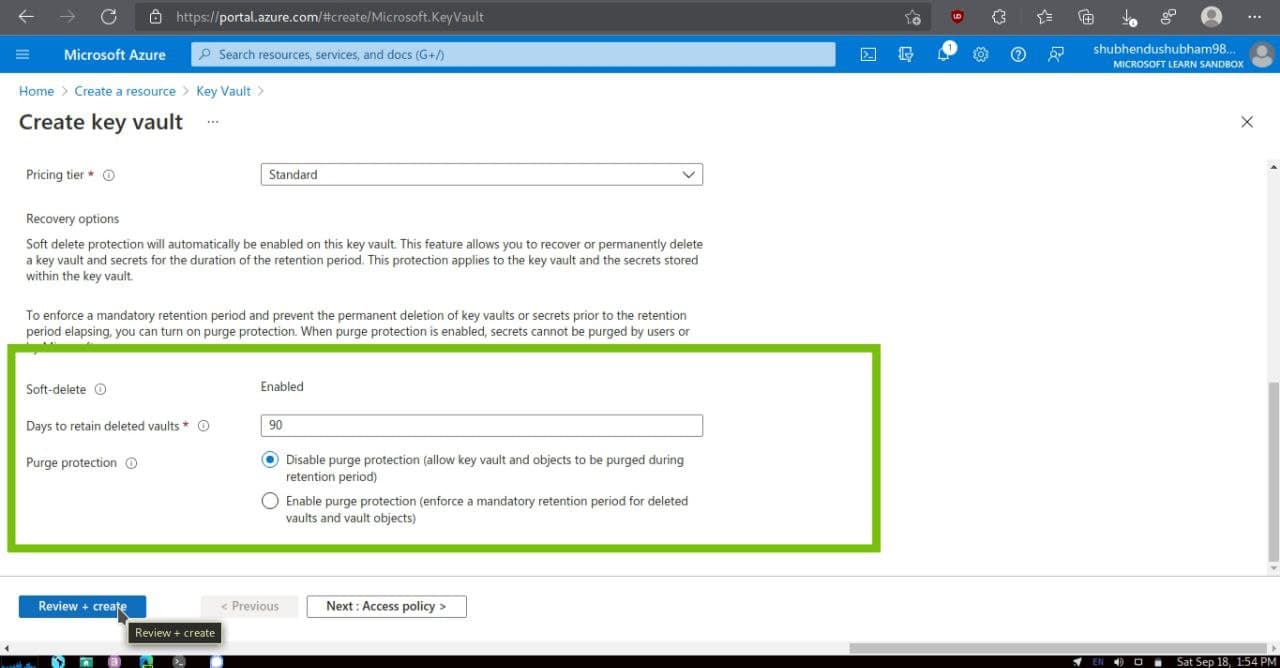
-
Select Review + Create and after passing validation,select Create.Wait for deployment to successfully complete.
-
Select Go to resource
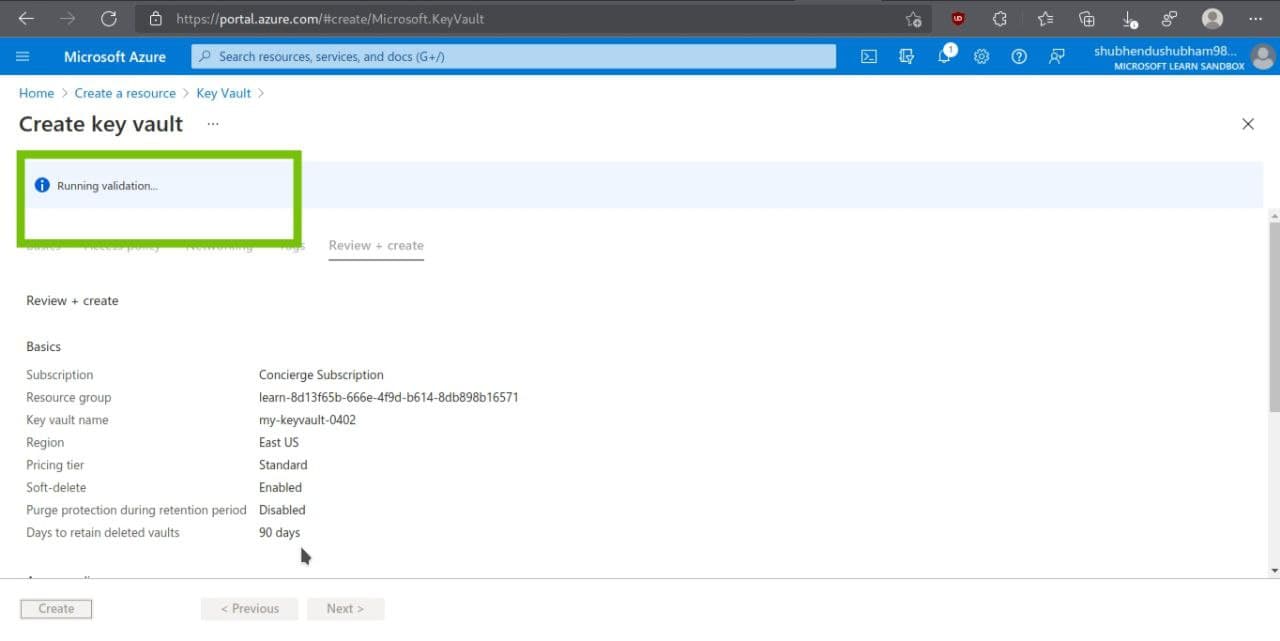
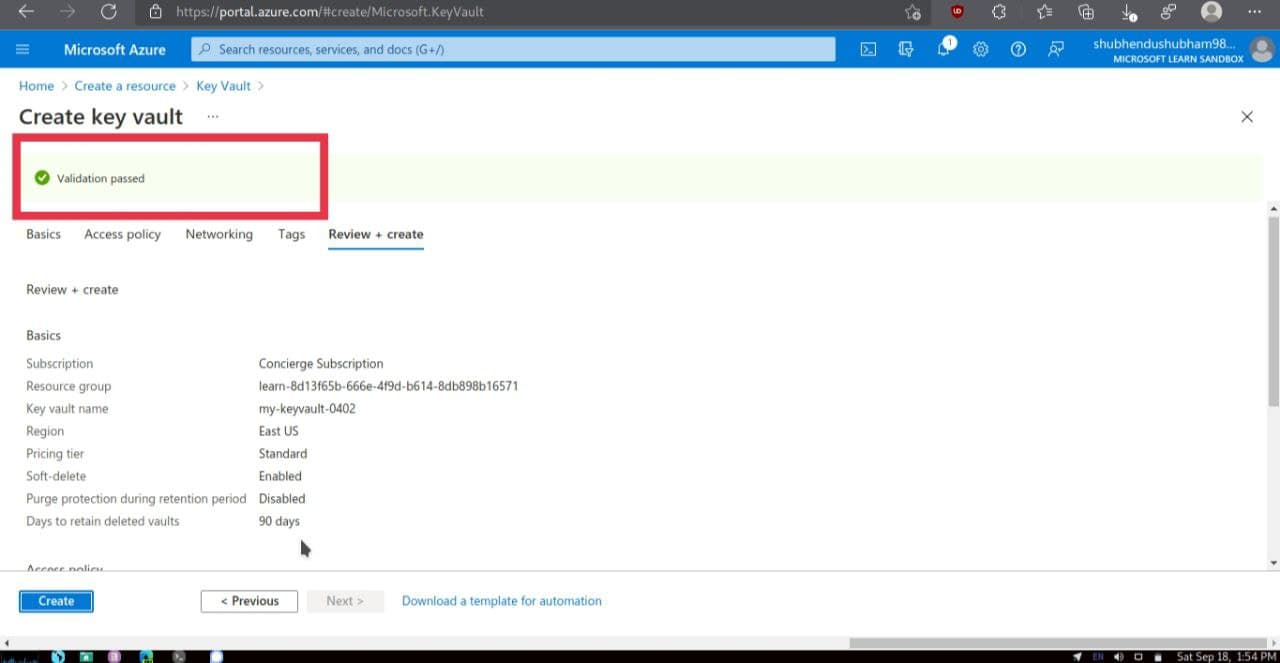
here, will appear some details about your key vault eg, Vault URI field shows the URI that your application can use to access your vault from the REST API.
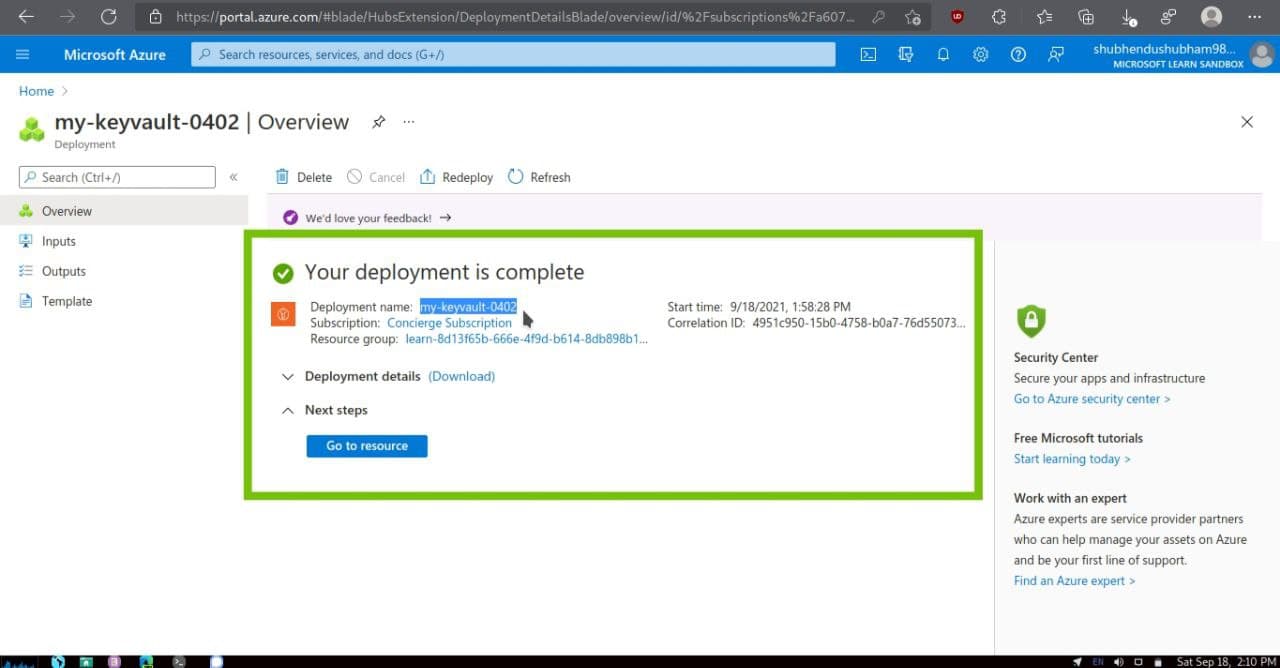
- As an optional step, on the left menu pane,under Settings, examine some of the other features.
Adding a password to the key vault
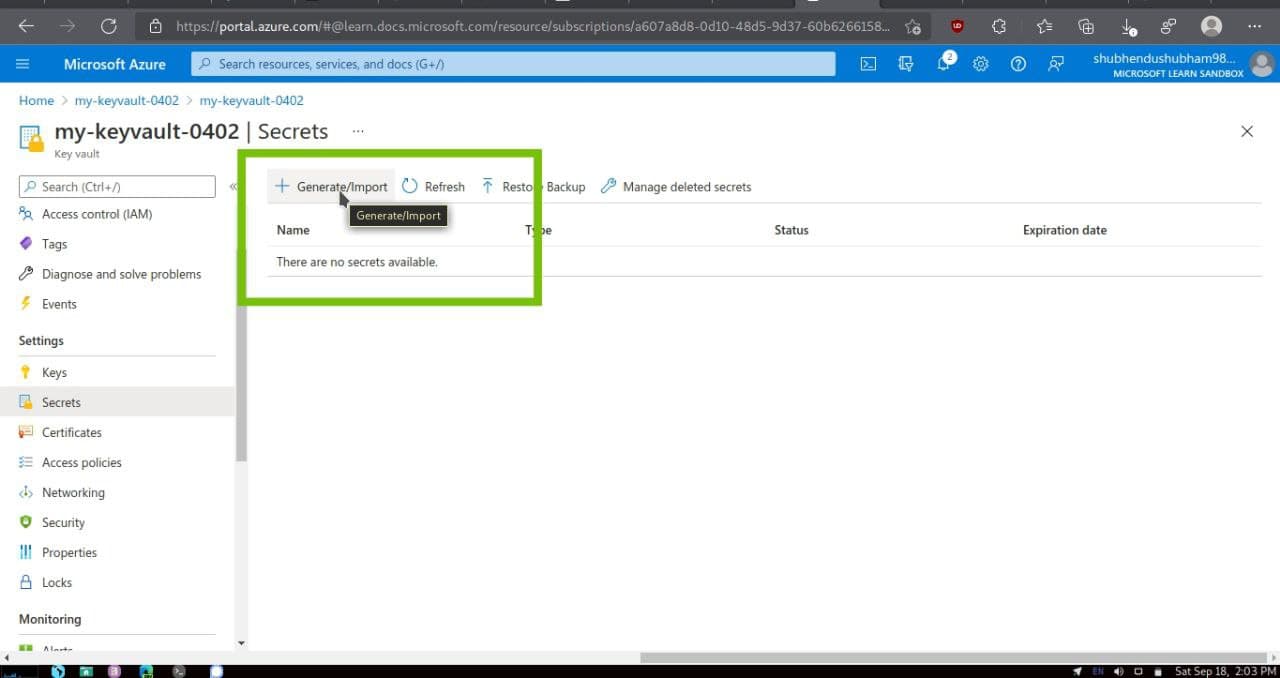
- On the left menu pane,under Settings,select Secrets. The Secrets pane for your key vault appears.
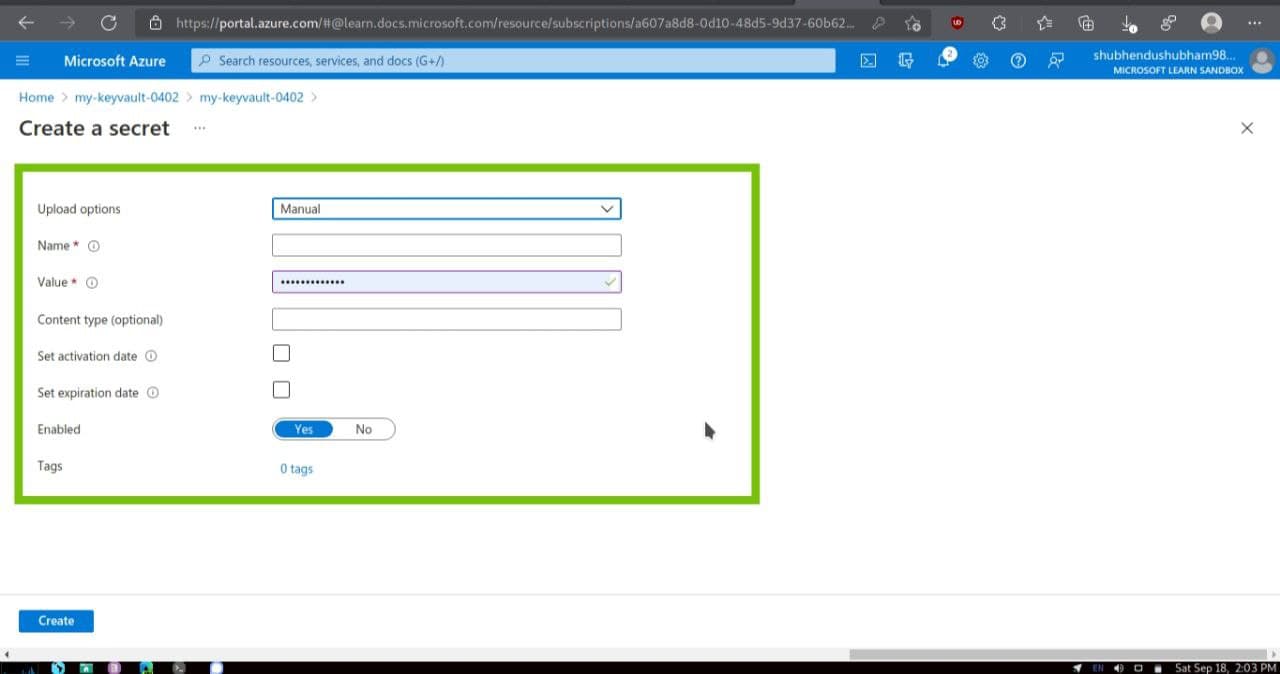
- From the top menu bar, select Generate/Import.The Create a secret pane appears.
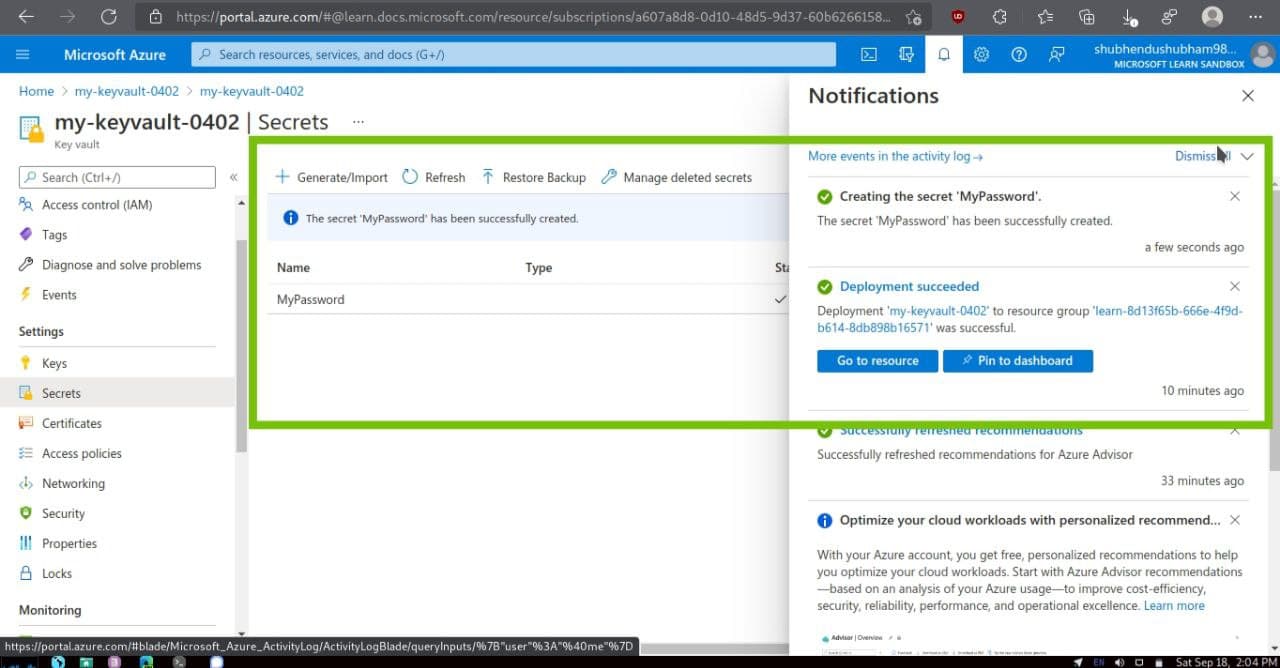
Fill these details accordingly :-
| Settings | Value |
|---|---|
| Upload Options | Manual |
| Name | MyPassword |
| Value | hVFkk96 |
Accept the remaining settings at their default values.Notice that you can specify properties such as the activation date and the expiration date.You can also disable access to the secret.
- Select Create
Showing the Password
There are the 2 ways to access password from the Key Vault i.e
- from Azure portal
- Azure CLI
Being a linux distro user and Die hard fan of CLI, here I am gonna use Azure CLI to fetch password from Azure vault.
- Run Cloud Shell
- az keyvault secret show
–name MyPassword
–vault-name\ --query value \ --output tsv
**
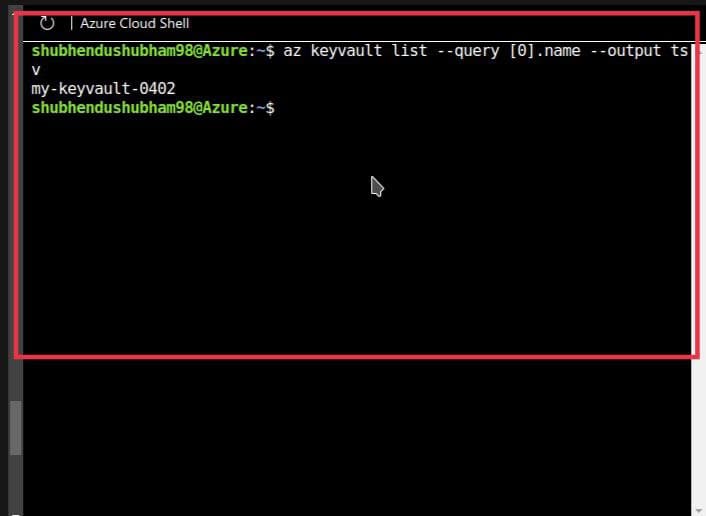
Output :-
hVFkk96
JSON View
Cleaning Up
The sandbox automatically cleans up your resources when you’re finished with this module.
When you’re working in your own subscription, it’s a good idea at the end of a project to identify whether you still need the resources you created. Resources left running can cost you money. You can delete resources individually or delete the resource group to delete the entire set of resources.


Comments