4 min to read
How to integrate Docker Scout with Azure Container Registry
Container Security

Before starting, let’s understand what exactly is Docker Scout? Docker Scout is a container image scanning tool built within Docker Desktop as well as CLI with mindset of Shift-Left approach.It lies on the top of the Docker ecosystem and helps developers to find container image vulnerabilities at the time of image build,thus helps organisation to ship secure entire supply chain.Now one might be confused is that Docker-Scout another CNAPP tool? As per official documentation,it uses SBOM(Software Bill of Material) with 17+ advisory Databases to analyze and scan images with real time CVEs updates.
Now let’s see how we can integrate with Azure Container Registry to scan real time image.
ACR+DockerScout is in Early Access phase at the time of writing this blog
Infra Prerequisites:
-
Resource Group (Make sure region of resource group should match with ACR region and ACR region integration is not available for all region so refer official docs)
- ACR (Azure Container Registry)
- Event Grid with System Topic Deployed
- Event Hub Namespace
- Inside ACR,enable Token from Repository Permission Blade
- Docker Hub account, if you don’t have create New one
- Docker socut logged in with Docker hub account
- Locally Docker Installed, if using Laptop CLI
LAB In this lab I have taken OWASP Juice Shop App as container image to scan with Docker Scout.
Azure Container Registry(Azure portal)
-
Go to Azure Portal and search for container Registry and create one.Just for testing I have allowed all public network access to registry from Networking blade,but in the production use private N/W

-
After successful ACR creation, you’ll get unique login server
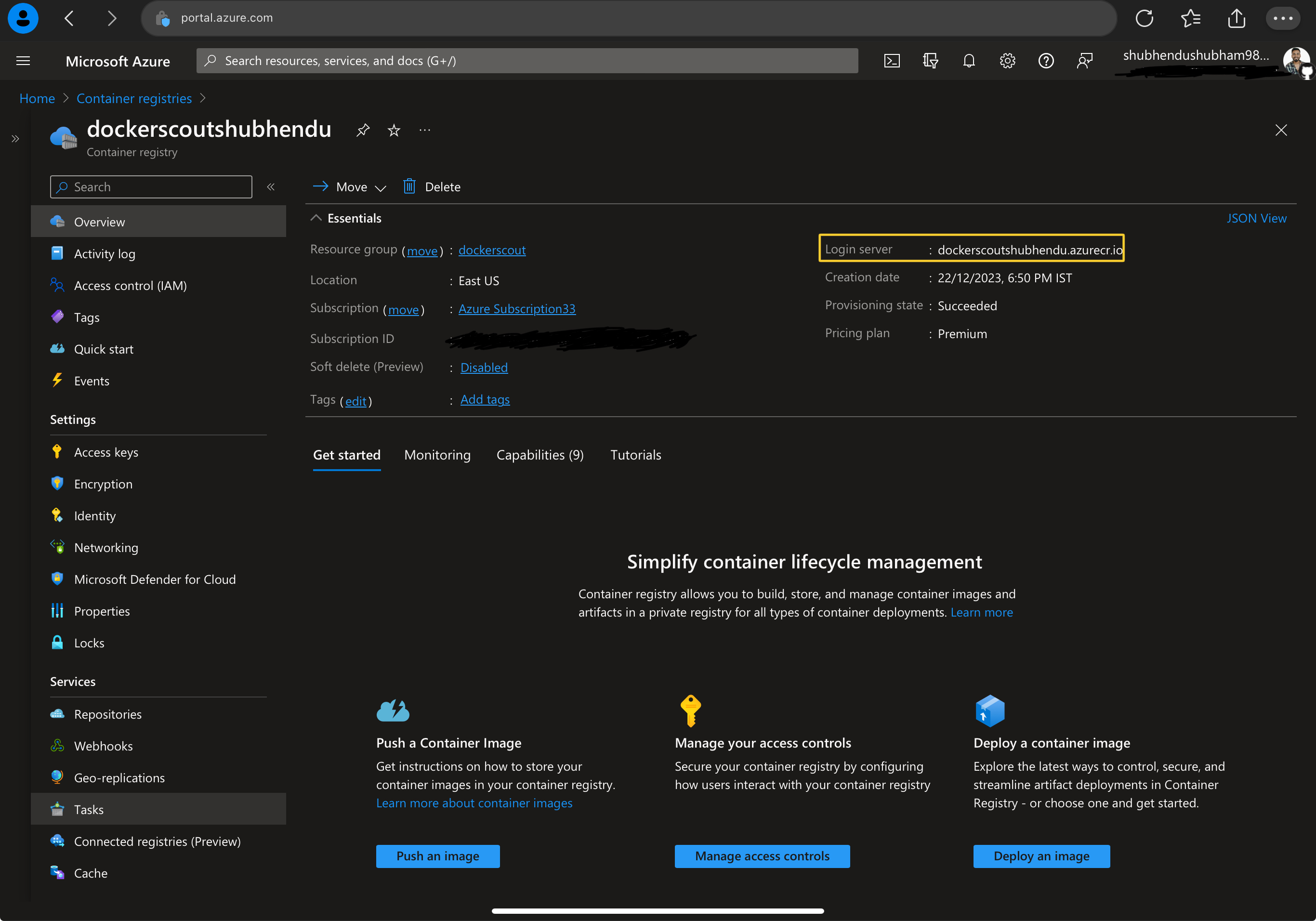
-
Now create a registry token from Repository permission blade,this token will be required during Docker Scout configuration. If you are using ARM template provided by Docker to deploy ACR then you can skip this step.

-
Now grab the container image of OWASP Juice APP, using docker pull command or else feel free to use own custom image.
docker pull bkimminich/juice-shop
- Now Run this Image locally
docker run --rm -p 3000:3000 -d bkimminich/juice-shop
You will see OWASP Juice Shop application can be accessible over port 3000. This is vulnerable application provided by OWASP for pentesting.
- Now tag this image and push it to ACR using following command
docker tag bkimminich/juice-shop dockerscoutshubhendu.azurecr.io/owasp:v1
Replace my loginserver with yours.
- Push it to ACR
docker push dockerscoutshubhendu.azurecr.io/owasp:v1

Confirm from Azure portal Repositories blade

Now let’s integrate ACR with SCOUT for Vulnerability scan
Docker Scout Integration
- Visit Docker Scout Dashboard, and Login with docker account and select Azure Container Registry Option
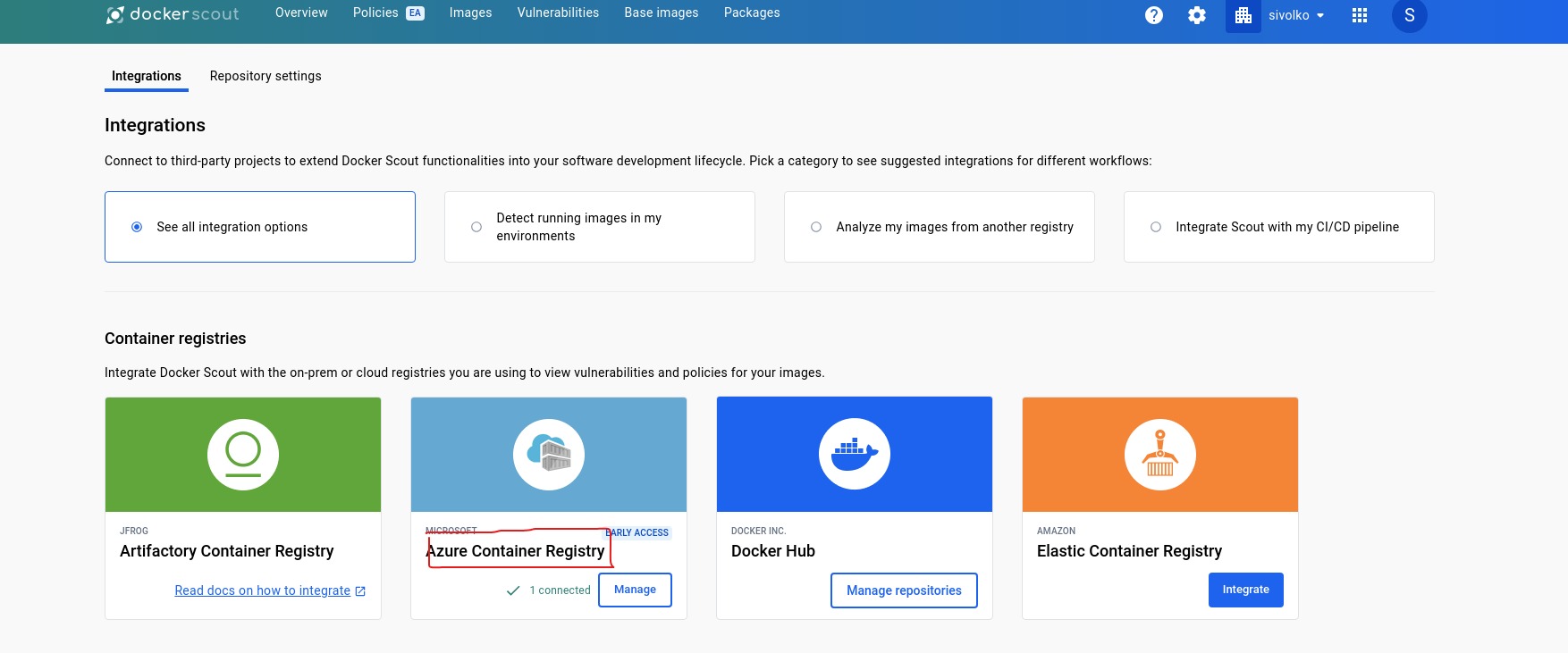
- Now Enter Registry Name,which is nothing but your login server from ACR, copy paste same
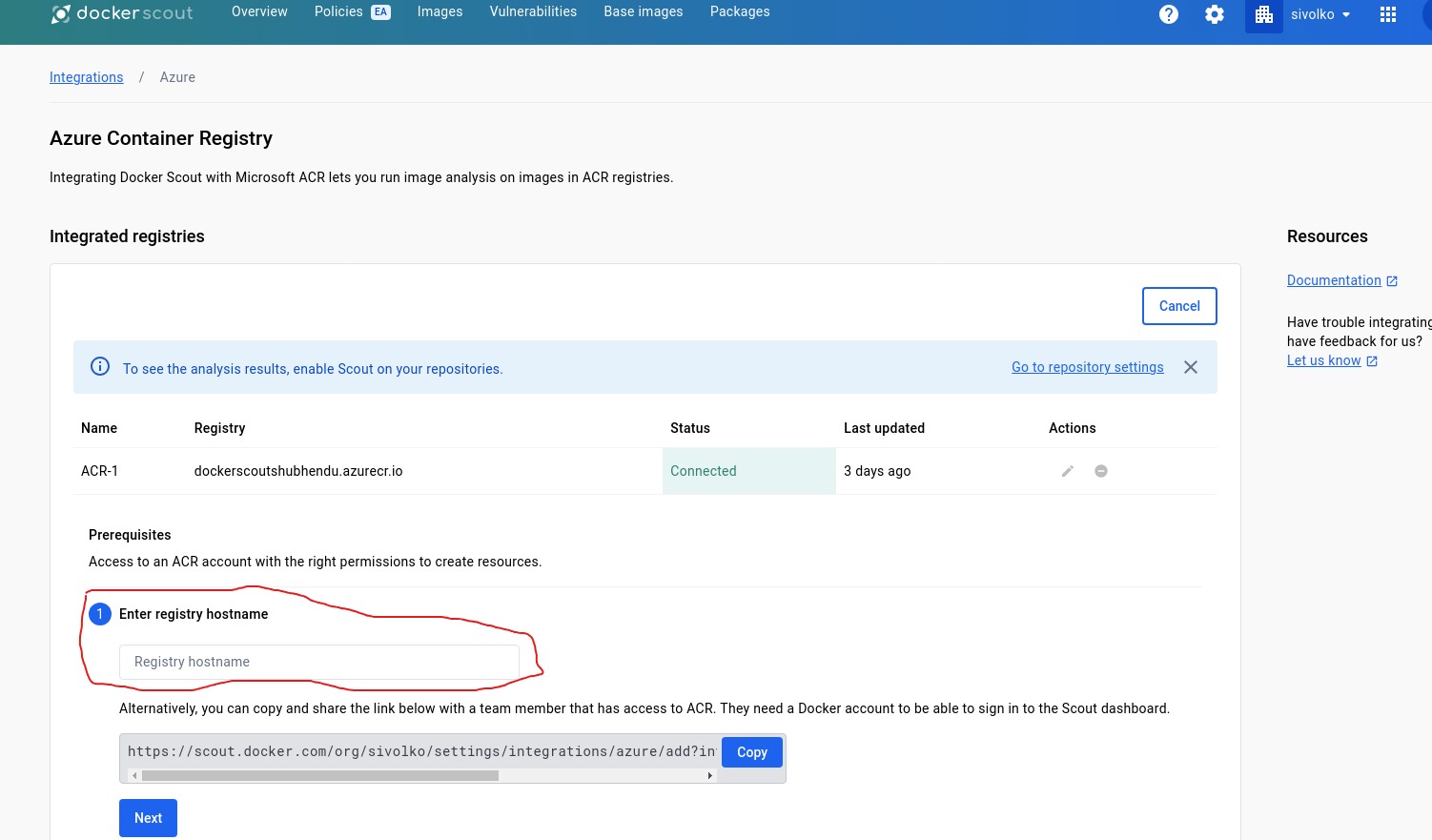
after that, you will get ARM template to deploy, basically this ARM template will deploy a Event Grid system topic from Azure Service Events and Registry token .
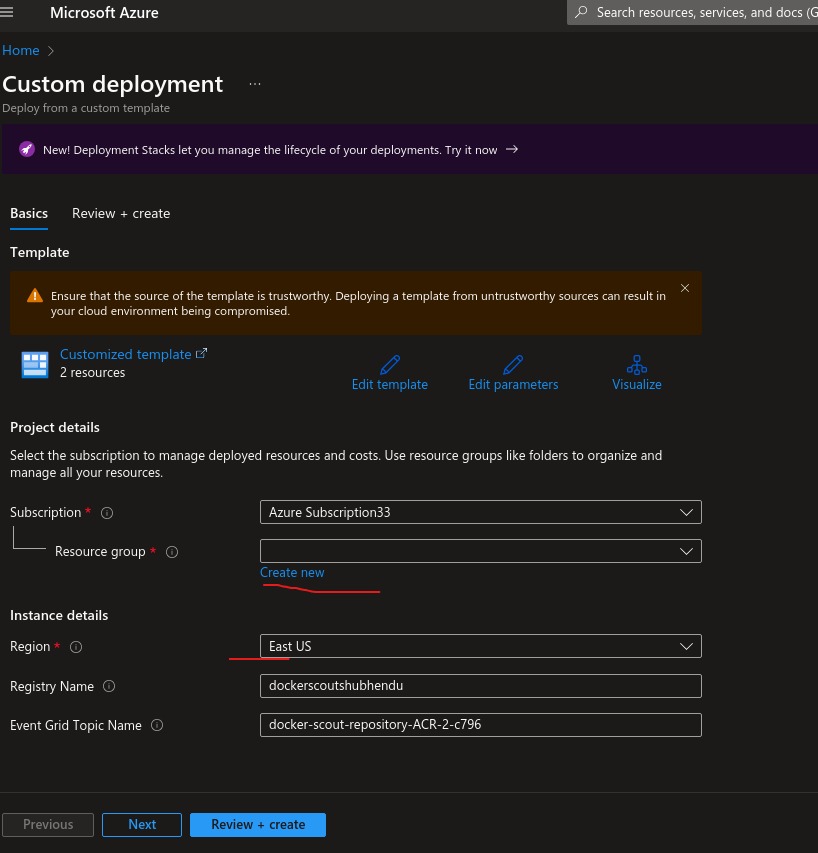
Make sure to deploy Docker Scout resources to the same resource group as the registry.Then review and create. After successful deployment go to your ACR–> Tokens from Repository Permission blade and copy token, then generate password. You can set password expiration date too. But remember to copy and save password locally, once window is close same password can’t be retrived. You need to regenerate.
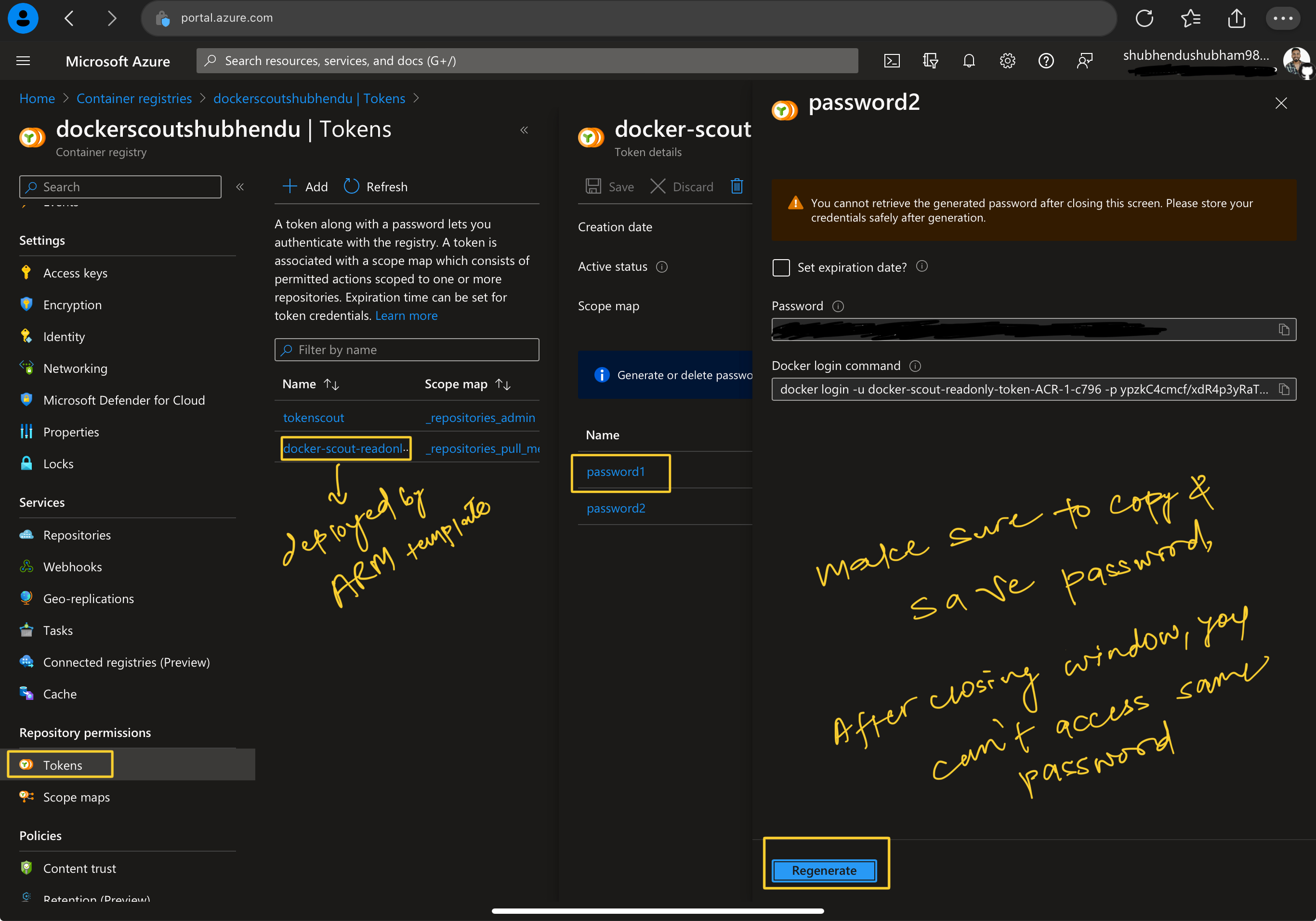
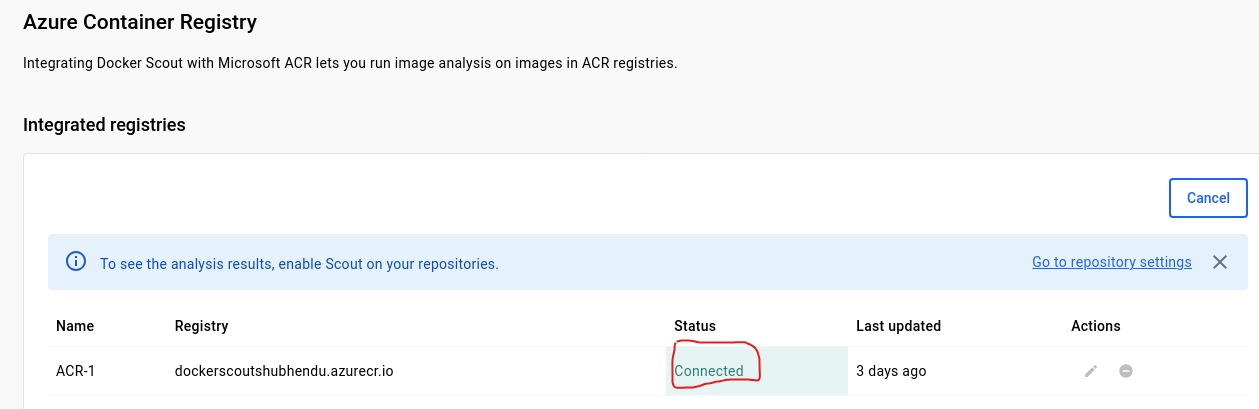
Copy the same Token/password put into Docker Scout Registry Token blade and click on enable integration.

After 5 min, status on Docker Scout will change to connected
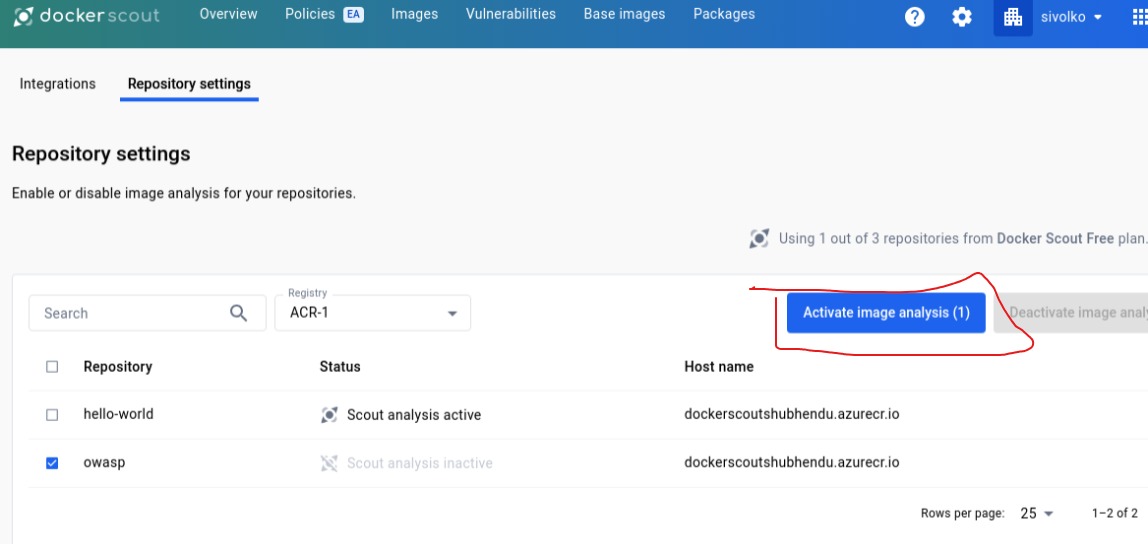
 Now to start SCAN,select Image and activate Scan Analysis
Now to start SCAN,select Image and activate Scan Analysis
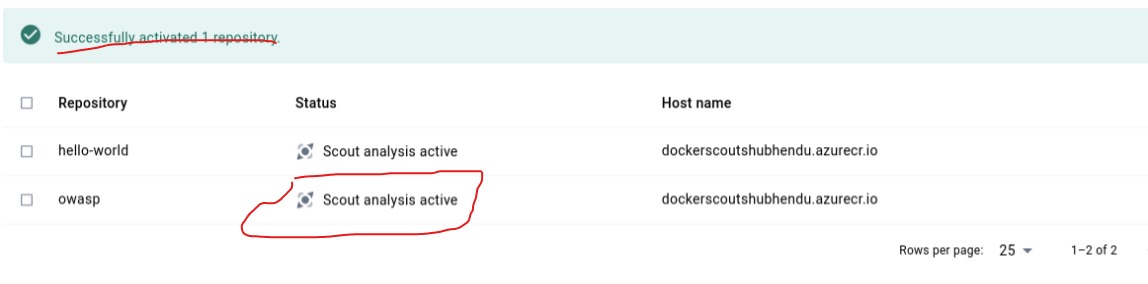
Jump over image blade,there our ACR image is scanned with list of vulnerabilities.

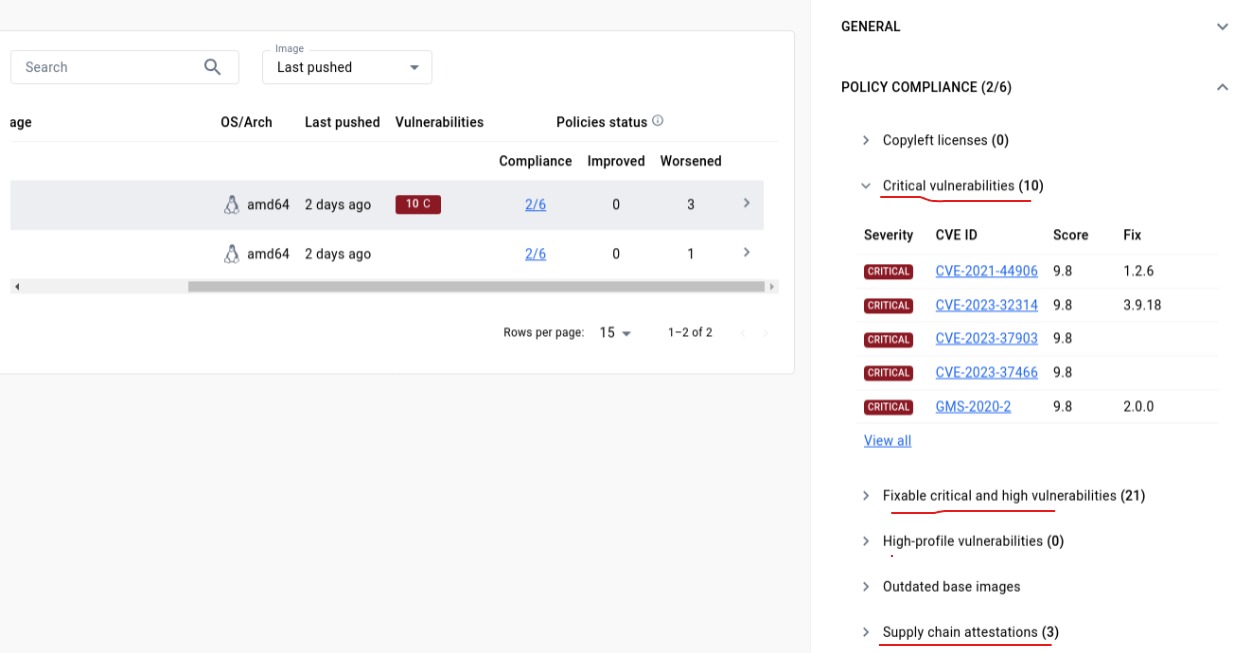
Jump over Vulnerabilites blade for more details
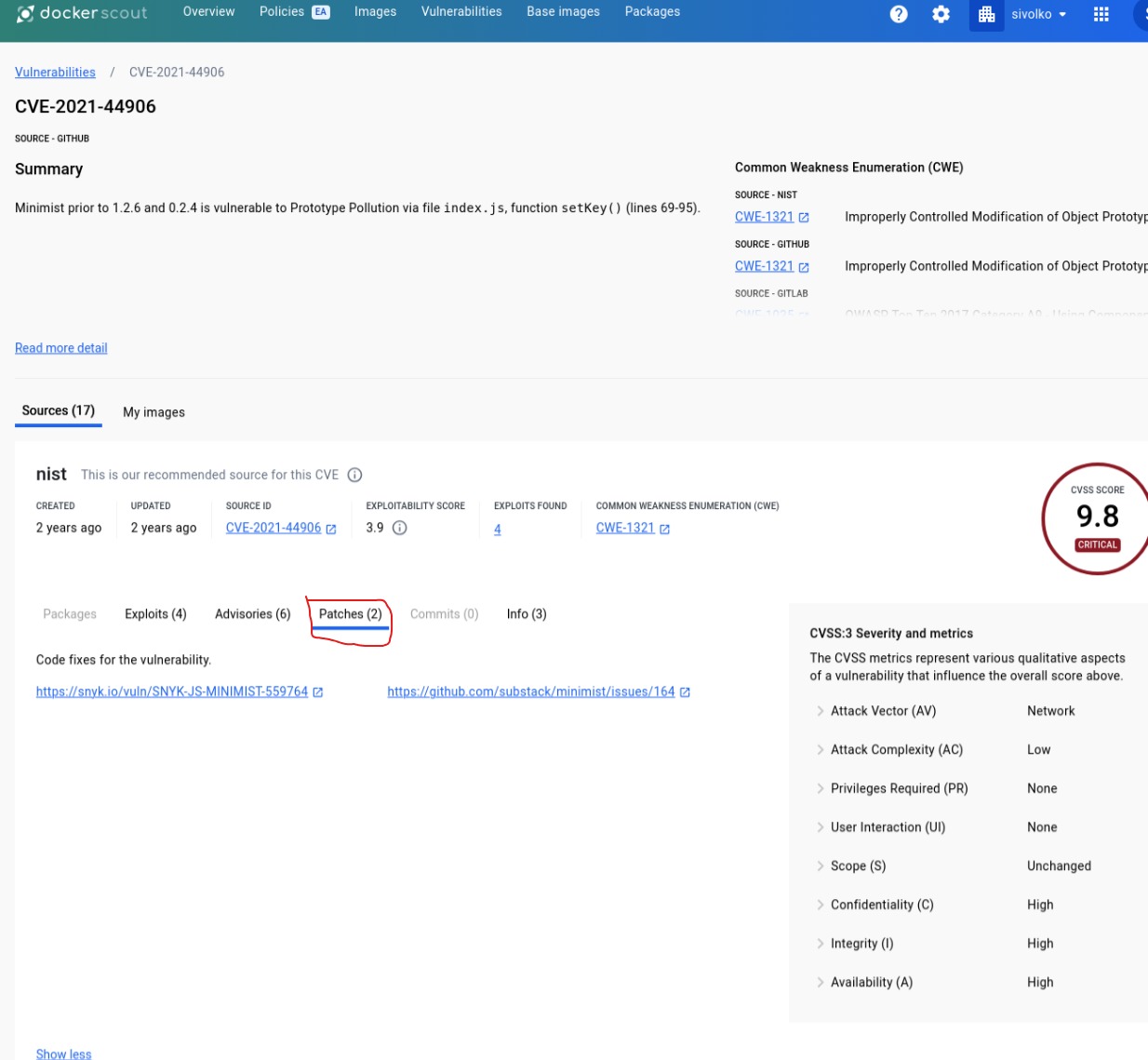
To mitigate vulnerabilities, jump to patch blade and follow the patch released by specific vendor.
We can check all centralised details from overview blade too.
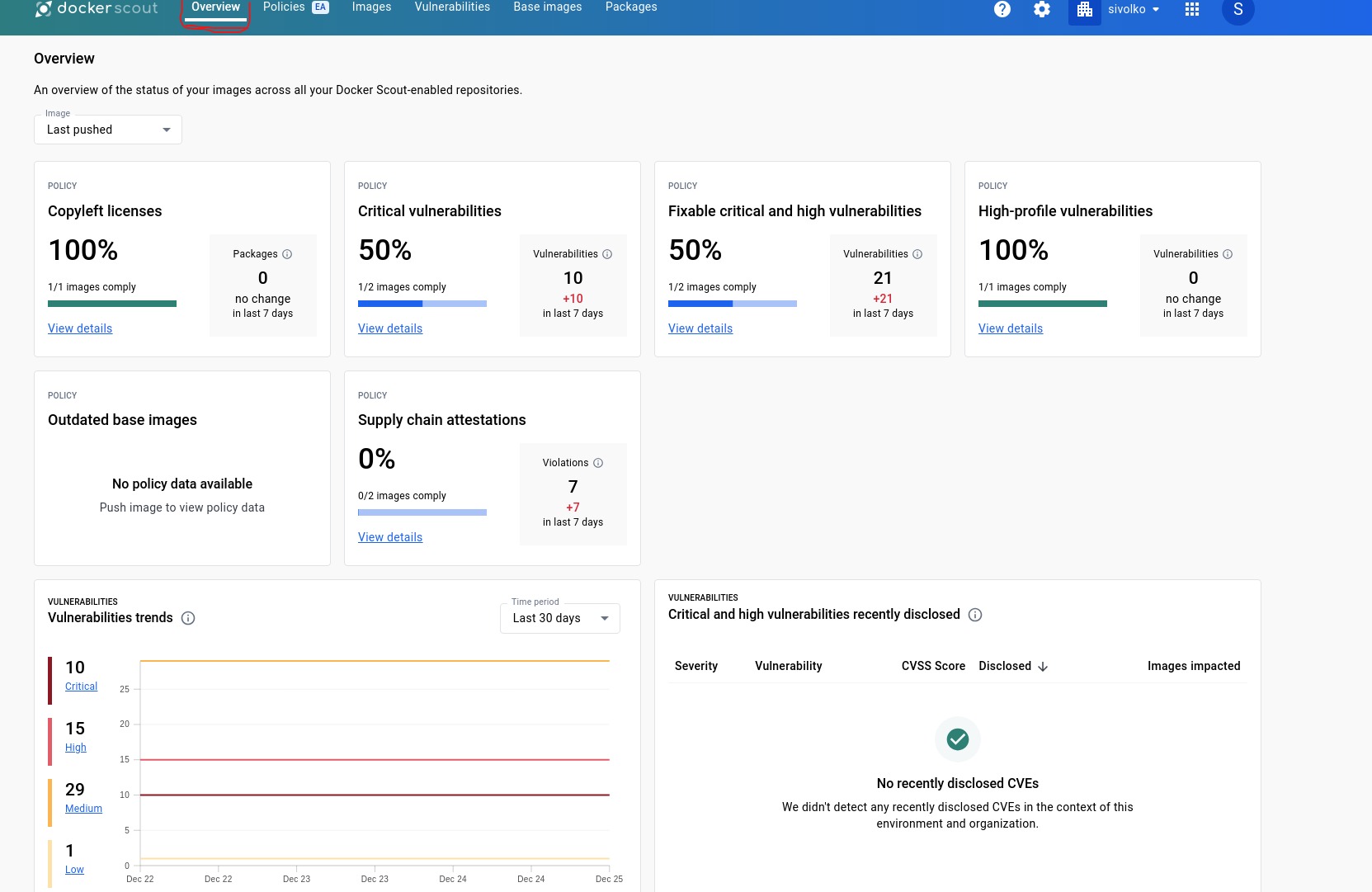
and we can deploy our own custom policies from Ploicies blade to set rules.
Thanks for reading blog, keep troubleshooting!


Comments